Another day, another hacker makes off with a few million customers’ data from Enormo Bank in the latest massive corporate cyber security breach. Small to Medium Size Businesses (SMBs) snicker to themselves and offer thanks to the sky that they aren’t big enough for hackers to pay attention to. If that’s your mindset, we’d like to be the first to tell you that your perception is wrong. Dead wrong.
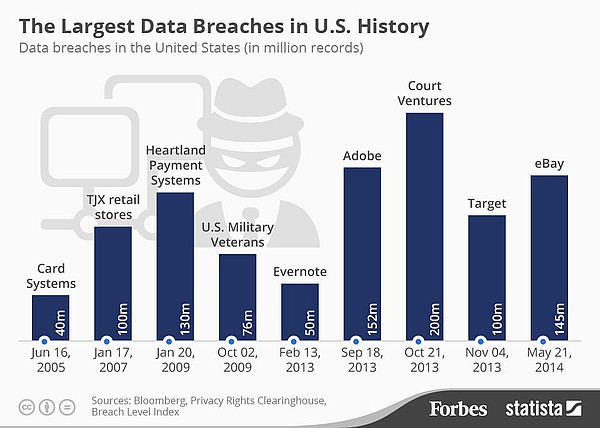
The reality, according to the US Congressional Small Business Committee, is that a full 71% of online security breaches are targeted at companies with fewer than 100 employees. Say what? You read correctly, so if the “we’re too small for the bad guys to pick on” mindset permeates your SMB, now might be a good time to put put down the energy drink, sit up straight, and pay close attention to these 7 Website Security Tips That Might Save Your Business from a Data Breach.
You’ll be glad you did.
#1 Firewalls Are Not Just A Good Idea
If you don’t have firewalls installed in your network, you might as well hop on the dark web right now and post all your passwords for any passing hacker to find. The reality is that you should consider a firewall your first line of defense in protecting customer data. As a quick review, a firewall is a security system – either hardware or software – that monitors data flow between your internal network and the internet and screens out suspicious activity based on predetermined security rules.
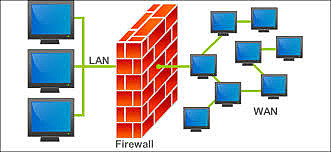
There are three areas to concentrate on when it comes to installing firewalls.
External Firewall: This type of firewall is normally found as part of a router or server. It sits outside your company’s network and prevents all kinds of malware attacks from ever reaching your system in the first place. If you’re not sure whether you have one or not, call up your web host and ask some questions.
Internal Firewall: This type of firewall takes the form of software installed on your network. While it performs a similar role to the external firewall, namely scanning for viruses, malware, and other cyber-nasties, it also should be set up to segment the network so that viruses, hacks, and the like can be quickly quarantined and the spread limited before it infects the entire system.
The third area to pay attention to is in regard to employees working from home who access the company network. Your overall security is only as good as the weakest link. It would be well worth the peace of mind to pay for next generation firewall protection in such instances.
Firewalls are intrinsically linked with your website/network’s hosting setup. For the few extra bucks it costs per month, you might consider leaving behind the days of shared hosting and upgrading to something more robust, either a dedicated server or virtual private server that allows more control over the specific security configurations.
#2 Secure Those Smart Devices
A Tech Pro survey in 2016 found that 59% of businesses follow a Bring Your Own Device (BYOD) policy. That’s a lot of potentially unsecured avenues into the company network wandering around the halls and offices. Obviously, crossing your fingers and hoping no bad guy notices this massive security failure is not sound policy, so what are you going to do? At this point in the Information Age, attempting to keep personal devices like smartphones, tablets, fitness trackers, and smart watches out of the workplace would likely result in a full-scale walkout of your entire workforce.
Here’s what to do.
Create a security policy that applies specifically to personal devices. Let employees know that it’s fine to BYOD but they must – repeat in caps for emphasis – MUST adhere to the rules that insure the safety of the network. Two specific steps to take are:
- Require all personal devices be set to automatically check for and install security updates.
- Require all personal devices adhere to the company password policy. You do have a password policy, right? It’s pretty important. We’ll talk about why in a bit.
If you start to feel like the Grinch with all these requirements, ask yourself this. Would I prefer to irritate a few employees with strict cyber security guidelines or let my most valuable business asset, customer data, waltz out the door? That’s what we thought.
#3 One Security Manual To Rule Them All
As mentioned, today’s SMBs often count data as the most precious business asset. A single employee prone to sloppiness with passwords or who adopts a haphazard attitude towards visually screening all emails for phishing attempts can literally torpedo your business. A word to the wise. Customers can be quite unforgiving and hesitant to further patronize a company that is perceived to play fast and loose with their personal information. In the case that your company requires professional services, a security software developer might be a good choice.
Now, more than ever, training to prevent online security breaches has to be taken seriously by management and every single employee from the most grizzled veteran to the snot-nosed newbie. You’ve got to have a printed policy manual that spells out the protocols to be followed and the repercussions for not following them up to and including firing. As you might have noticed, cyber-criminals are a savvy lot. They are forever testing your defenses and creating new ways to penetrate your network either through technology, guile, or a combination of the two.
It is incumbent on SMB managers and owners to update the manual regularly according to standard practices against hacker attempts, as well as devote an adequate amount of time to provide appropriate education during new employee onboarding processes. If you want this effort to be taken seriously, and you should, YOU have to take it seriously. At the very least, any employee who accesses the company network for any reason needs to be thoroughly versed in how to keep it secure. A large part of this security rests in the topic of password security, which is important enough to get its own category.
#4 If You Do Nothing Else, Have A Strong Password Policy
Here are a few statistics that go a long ways towards illuminating exactly why a SMB might have a problem when it comes to cyber security.
- A 2016 Verizon report found that 63% of data breaches were caused by weak, lost, or stolen passwords. This is a problem.
- A Ponemon Institute report claims that 65% of companies with a password policy in place don’t enforce it. This is an even bigger problem.
Where do we even start with this? Yes, employees will complain to the high heavens if you require them to create more complex passwords than “1234” and change them regularly but, at the risk of sounding like a broken record, are you more concerned with minor worker irritation or the takeover of your network by hostile forces? If you said the former, we’d like to politely suggest you sell your business immediately.
Password security needs its own section in the security manual and best practices should be followed. This means you should require:
- Passwords be changed every 60-90 days
- Passwords be at least 8 characters in length but longer is better
- Passwords include upper and lower case letters, numbers, and special characters
To revisit that earlier number, once you go to the trouble of creating a strong password policy, don’t be part of the 65% who don’t enforce it. That’s just silly.
Password Managers: We hate to leave this section without mentioning password managers. Available as installed software, a cloud service, or even a physical device, these programs help you generate and retrieve complex passwords. It does just what the name claims, which is manage your passwords, and it seems that most of us could use help in that area.
Read more about this top (and inexpensive) online security precaution from Consumer Reports.
#5 Backups? Now More Than Ever
You’ve decided to follow each of our suggestions so far precisely, exactly, and completely, with no deviation. You can now breathe a huge sigh of relief that your company network is unassailable. Why not lean back and prop your feet up? Here’s why not. Despite the best intentions of you and your entire staff, there’s at least a possibility that a hacker will still manage to sneak in and create a ruckus. As we said, these guys and gals are a clever bunch who are dedicated to criminal mischief. Once inside, they can do a variety of damage from recording password keystrokes to using your resources to launch an all-out ‘bot attack to wiping your server clean.
At that point, you’re going to wish you could roll back the system to a previous point in time before the hacker got his hands into the mix. You have been regularly backing up everything to the cloud and even storing another copy in a physically remote location, right, because fires and floods happen? If you’re not doing it now, give a strong thought towards backing up word processing documents, spreadsheets, databases, financial records, HR files, and accounts receivable/payable.
With cloud backup services getting more affordable every day, there is no excuse to not implement a comprehensive backup strategy that lets you return your system to operational status quickly in the event of a network penetration. Unless you like reconstructing every file you use from memory…
#6 Anti-Malware Is Not Optional
Okay, choosing whether or not to install anti-malware IS optional. Instead, we should have said that deciding in the negative is a bad idea. Anti-malware protects against phishing attacks, which have become one of the favorite tactics employed by hackers for one reason – they work like a charm. For proof, we turn once again to the 2016 Verizon report. According to this survey, 30% of employees have opened phishing emails, which was up 7% from the previous year!
For review, phishing is a technique by which a hacker sends an email intended to entice an employee to clink on a link in it. Taking the bait triggers a malware installation on the network and the hacker is in. That’s a bad thing. The first line of defense against phishing is to train your employees not to click on anything in an email unless they are double darn sure it’s legit.
Considering that 30% of employees are essentially inviting a hacker into the network, anti-malware is your best bet at intercepting and shutting down the rogue software installation before it can be completed. Pay particular attention to employees in the positions that hackers love to phish: CEOs, admin assistants, salespeople, and HR. These have been shown to be particularly popular targets since they often have access to the soft underbelly of the best parts of the network.
But don’t make the mistake of assuming everyone else is immune. Any employee with access to any part of the network is a potential target.
#7 Multi-Factor Authentication – Rapidly Becoming Best Practice
In recent years, multi-factor authentication (MFA) has appeared as a bright spot on the radar of those concerned with their network’s security. Yes, it might be a bit of a hassle but it is an almost fail-safe way to secure the login process. There are plenty of permutations of the exact process but here’s how one company’s login might go:
- User enters password the traditional way by typing it into the system’s prompt
- A second, one-time password is generated and sent to the user’s cell phone
- User is taken to the final login page where he/she enters the code from their phone
- Entry to the network is granted
An even easier way to implement MFA is simply to have the employee’s cell phone number serve as the second login. The thinking here is that a hacker is extremely unlikely to have access both to the first login and the cell phone number. This extra layer of protection is relatively simple to activate on most systems and greatly beefs up password security.
Much of the pioneering work in this field comes from Google, which recently completed a year-long stretch where not a single one of its 85,000 had their Gmail account hacked. They did it through the use of a physical security key called Titan that plugs into a USB port. Even with a username and password, a hacker could get no further into the account without having physical access to the key.
Final Thoughts
The Big Picture idea is that those involved in SMB have to keep in mind that website and network security does not involve throwing a big switch and then never having to worry about cyber criminals again. It’s an iterative process in which the goal line continues to move forward each time you take a step towards it. There is no set it and forget process. The bad guys never stop testing and learning, becoming more sophisticated with their efforts, so you can’t either. Nowadays companies have to comply with data privacy regulations, so having a data governance system will also ensure that all data being used is collected and managed in the right way.
If you don’t already, either you or someone you designate should keep a finger on the pulse of the cyber security industry in order to take note of new methods of attack and prevention as they arise. In a world where your opponent never stops learning, you can’t afford to either. If you care for your business, complacency is not an option when it comes to making sure your private network and data stays that way, private.
Share this article
7 Ways To Speed Up Your Website Right Now
Discover 7 effective ways to speed up your website instantly! Learn how to reduce HTTP requests, optimize images, enable browser caching, use Gzip compression, minimize CSS, and upgrade your hosting. Boost your site's performance for a seamless user experience now!
How To Find Affiliates to Sell Your Products
Discover over 10 successful strategies for finding high-quality affiliates in 2024 to boost your product sales. Learn to leverage influencers, join affiliate networks, and enhance your reach through SEO and social media. Maximize revenue with transparency and ongoing monitoring in your affiliate marketing program.
7 Untapped Traffic Sources For Marketing Your Website
Discover seven untapped traffic sources to boost your website's visibility with expert tips from Neil Patel. Explore innovative strategies using Quora, Reddit, forums, LinkedIn, small blogs, StumbleUpon, and Facebook groups to drive more traffic and enhance your marketing efforts. Learn how engaging with niche communities can lead to increased website traffic and success in affiliate marketing. Don't miss out on these powerful opportunities!
Why Protecting Your Business Is Essential If You Plan To Sell
Protect your business to boost its value and ensure a successful sale. Learn strategies to manage risks, diversify revenue streams, and plan for unexpected events. Discover how contingency planning, insurance, and process optimization can safeguard your business's future.
Best 7 social media organization tips and tricks for businesses
Discover the top 7 social media organization tips for businesses to elevate your marketing strategy. Learn how to build a cohesive plan, utilize editorial calendars, leverage scheduling and automation tools, and analyze social media metrics to enhance brand engagement and growth. Transform your social media presence with expert guidance.
13 Tips To Successful Affiliate Marketing
Discover the top 13 strategies for successful affiliate marketing and unlock your potential to earn online. Learn how to build trust, choose the right products, and engage your audience effectively. Perfect your timing and diversify your promotion platforms to maximize your earnings. Visit Post Affiliate Pro for expert tips and start your journey to affiliate marketing success today!