
7 Security Tips to Prevent Business Data Breaches
Protect your small business from data breaches with 7 essential security tips: firewalls, password policies, backups, and more.

why SMBs are the primary targets for cybercriminals, the vulnerabilities they face, and how to protect your business from cyber threats with proven security

Small and medium-sized businesses (SMBs) have become the primary target for cybercriminals, and the reason is simple: they represent the perfect storm of opportunity and weakness. These organizations typically hold valuable customer data, financial information, and intellectual property—assets that hackers can monetize quickly. However, unlike large enterprises with dedicated security teams and sophisticated defense systems, SMBs often lack the resources to protect these assets adequately. 71% of all data breaches target companies with fewer than 100 employees, yet many of these organizations operate with outdated systems, minimal IT staff, and virtually no formal cybersecurity strategy. The gap between the value of data SMBs possess and the strength of their defenses creates an irresistible target. Perhaps most alarming, 51% of SMBs have implemented no cybersecurity measures whatsoever, leaving their networks essentially wide open to attackers. This vulnerability gap isn’t accidental—it’s the direct result of limited IT resources, budget constraints, and a lack of employee training on security best practices. For hackers, SMBs represent low-hanging fruit: high reward with minimal effort required to breach their defenses.
From a purely economic standpoint, attacking SMBs makes far more sense to cybercriminals than targeting large enterprises. While a major corporation might have sophisticated security systems that take months to penetrate, an SMB can often be compromised in hours or days. Attackers operate on a volume-based model: rather than spending significant time and resources to breach one Fortune 500 company, they can compromise dozens of small businesses in the same timeframe, generating substantial cumulative profits. The financial incentive is compelling because the risk-to-reward ratio heavily favors the attacker. Consider the economics:
| Attack Target | Effort Required | Potential Payout | Risk Level | Profitability |
|---|---|---|---|---|
| Large Enterprise | 6-12 months | $500K-$5M | Very High | Moderate |
| Mid-Market Company | 2-4 months | $100K-$500K | High | Good |
| Small Business | 1-7 days | $10K-$100K | Low | Excellent |
| Multiple SMBs (10) | 2-3 weeks | $100K-$1M | Low | Excellent |
This table illustrates why attackers have shifted their focus downmarket. The combination of quick access, reasonable payouts, and minimal detection risk makes SMBs the most profitable targets in the cybercriminal economy.
The financial reality facing most SMBs creates a perfect environment for successful cyberattacks. While large enterprises allocate 10-15% of their IT budgets to cybersecurity, SMBs typically spend less than 5%, and many spend nothing at all. This disparity means that small businesses often operate with outdated software, unpatched systems, and minimal security infrastructure. Many SMBs employ a single IT person or outsource to a managed service provider who handles multiple clients, leaving security as an afterthought rather than a priority. The average cost of implementing enterprise-grade security solutions—firewalls, intrusion detection systems, security information and event management (SIEM) platforms—can exceed $50,000 annually, a prohibitive expense for businesses with thin margins. SMBs spend an average of $1,500-$5,000 per year on cybersecurity, compared to $10 million or more for large enterprises. This funding gap directly translates to vulnerability: outdated operating systems, unpatched software, lack of backup systems, and no dedicated security monitoring. When budget constraints force SMBs to choose between investing in growth and investing in security, security almost always loses—until a breach forces a painful reckoning.
While technology plays a role in cybersecurity, the human element remains the weakest link in most SMBs’ defenses. Employees are often the gateway through which attackers gain access to networks, and SMBs typically lack the resources to provide comprehensive security training. The statistics are sobering:

The impact is staggering: SMB employees face 350% more cyberattacks than their enterprise counterparts, largely because attackers know these workers receive minimal security training. A single employee clicking a malicious link or opening an infected attachment can compromise an entire network. Unlike large organizations that conduct regular security awareness training and implement strict access controls, SMBs often operate on trust and convenience, allowing employees to use personal devices, access systems remotely without proper authentication, and share credentials. This human vulnerability is often easier to exploit than technical security flaws, making employee education one of the most critical—yet most neglected—aspects of SMB cybersecurity.
Hackers have discovered that SMBs serve another valuable purpose beyond direct exploitation: they function as gateways to larger, more lucrative targets. Many small businesses work as vendors, suppliers, or service providers to larger enterprises, creating trusted relationships and network connections. Attackers exploit these relationships by compromising the SMB first, then using that access to infiltrate the larger organization. This supply chain attack strategy has become increasingly common and devastatingly effective. A hacker might spend weeks trying to breach a Fortune 500 company’s heavily defended network, only to succeed in hours by compromising a small vendor that has direct access to the enterprise’s systems. The 2020 SolarWinds breach exemplified this approach: attackers compromised a software company’s update mechanism, which then infected thousands of enterprise customers. For SMBs, this reality means they’re not just targets for their own data—they’re targets because of the valuable connections they maintain. A small accounting firm, IT consultant, or logistics provider might hold the keys to accessing much larger organizations. This dual threat makes SMBs attractive targets regardless of their own data value, as attackers view them as stepping stones in a larger campaign.
The financial consequences of a cybersecurity breach can be catastrophic for SMBs, often proving fatal to the business itself. Unlike large enterprises that can absorb losses and recover from breaches, small businesses frequently lack the financial reserves to survive the combined impact of direct costs, downtime, and reputational damage. The average cost of a data breach for SMBs is $3.31 million, a figure that represents multiple years of profit for many small organizations. Beyond the direct costs of breach remediation, forensic investigation, and notification, SMBs face significant indirect expenses: lost productivity during system downtime, lost revenue from customers unable to access services, and the cost of implementing security improvements to prevent future breaches. 60% of SMBs that experience a significant breach close their doors within six months, unable to recover financially or rebuild customer trust. The range of breach costs is wide—95% of incidents cost between $826 and $653,587—but even the lower end of this range can devastate a small business. Regulatory fines add another layer of financial pain: GDPR violations can result in fines up to 4% of annual revenue, while HIPAA breaches can cost $100-$50,000 per record exposed. The reputational damage is equally severe, as customers lose confidence and take their business elsewhere. For SMBs, the question isn’t whether they can afford to invest in cybersecurity—it’s whether they can afford not to.

SMBs face a diverse array of cyberattacks, each exploiting specific vulnerabilities in their defenses. Ransomware attacks target organizations with fewer than 1,000 employees in 82% of cases, making SMBs the primary victims of this particularly destructive attack type. Ransomware encrypts an organization’s files and systems, rendering them inaccessible until the victim pays a ransom—often $5,000 to $500,000 or more. Malware represents another significant threat, with 18% of all malware attacks targeting SMBs, designed to steal data, monitor activity, or provide attackers with persistent access. Phishing attacks remain the most common entry point, using deceptive emails to trick employees into revealing credentials or downloading malicious files. DDoS (Distributed Denial of Service) attacks overwhelm SMB websites and services with traffic, causing outages that disrupt business operations and damage reputation. SQL injection attacks exploit vulnerabilities in web applications to access databases containing customer information and financial records. Each of these attack types is particularly effective against SMBs because they lack the sophisticated detection and response systems that enterprises deploy. A large organization might detect and contain a ransomware infection within hours; an SMB might not discover the attack until files are already encrypted and the ransom demand appears on their screens. The variety of threats means SMBs must defend against multiple attack vectors simultaneously, a challenge that exceeds the capabilities of most small IT teams.
One of the most dangerous misconceptions in the SMB community is the belief that “we’re too small to be targeted by hackers.” This false sense of security leads business owners to deprioritize cybersecurity investments and ignore warning signs of compromise. 59% of SMBs with no cybersecurity measures in place believe their size protects them from attacks, a belief that directly contradicts the data showing SMBs are the primary targets. This misconception stems from a misunderstanding of how cybercriminals operate: attackers don’t carefully select targets based on size; they use automated tools to scan networks for vulnerabilities and exploit any weakness they find. A small business with an unpatched server is just as attractive to an attacker as a large business with the same vulnerability—perhaps more so, because the small business is less likely to have detection systems in place. The “we’re too small” mentality creates a vicious cycle: because business owners believe they’re not at risk, they don’t invest in security; because they don’t invest in security, they become increasingly vulnerable; and because they’re vulnerable, they become targets. This false sense of security is particularly dangerous because it prevents SMBs from taking even basic protective measures—keeping software updated, implementing strong passwords, training employees on phishing awareness—that would significantly reduce their risk. The reality is that SMBs aren’t protected by their size; they’re targeted because of it.
Beyond the direct threat of cyberattacks, SMBs face increasing regulatory pressure to implement adequate cybersecurity measures. Regulations like GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), PCI-DSS (Payment Card Industry Data Security Standard), and industry-specific requirements impose strict security standards and carry severe penalties for non-compliance. A breach that exposes customer data can result in regulatory fines that dwarf the cost of the breach itself: GDPR violations can result in fines up to €20 million or 4% of annual global revenue, whichever is higher. For SMBs handling healthcare data, HIPAA violations can result in civil penalties ranging from $100 to $50,000 per record exposed. PCI-DSS requirements apply to any business that accepts credit card payments, mandating specific security controls and regular audits. These regulatory requirements create a dual burden for SMBs: they must invest in security to protect against attacks, and they must invest in compliance to avoid regulatory penalties. Many SMBs lack the expertise to navigate these complex requirements, leading to unintentional non-compliance that exposes them to fines even without a breach occurring. The regulatory landscape continues to evolve, with new requirements emerging regularly, making it increasingly difficult for SMBs to stay compliant without dedicated resources or external expertise.
While the threat landscape for SMBs is undeniably challenging, organizations can significantly reduce their risk through strategic security investments and the right tools. For businesses operating affiliate networks or partner programs, security becomes even more critical, as these networks handle sensitive partner data, commission information, and customer details. PostAffiliatePro recognizes this unique challenge and has built security into its core platform to protect affiliate networks and partner ecosystems. A comprehensive defense strategy should include multi-factor authentication (requiring multiple forms of verification before granting access), data encryption (protecting sensitive information both in transit and at rest), and continuous monitoring (detecting suspicious activity in real-time). For affiliate networks specifically, PostAffiliatePro provides built-in security features that protect partner data, prevent unauthorized access, and maintain compliance with industry regulations. The platform’s approach to security includes role-based access controls, audit logging, secure API connections, and regular security updates—features that would cost SMBs tens of thousands of dollars to implement independently. By choosing a partner platform that prioritizes security, SMBs can leverage enterprise-grade protection without the enterprise-level budget. The key to effective cybersecurity isn’t perfection; it’s implementing layered defenses that make attacking your organization more difficult and costly than attacking competitors. For SMBs operating in the affiliate space, PostAffiliatePro provides that critical foundation, allowing business owners to focus on growth while their partner network remains secure.
Hackers target SMBs because they offer the best risk-to-reward ratio. Small businesses typically have valuable data but weaker defenses than enterprises, making them easier to breach. Attackers can compromise multiple SMBs in the time it takes to penetrate one large corporation, generating substantial profits with minimal risk of detection or legal consequences.
While malware is technically the most common attack type at 18%, phishing attacks are the most effective entry point for cybercriminals. Phishing exploits the human element by tricking employees into revealing credentials or downloading malicious files. SMB employees receive 1 in 323 emails that are malicious, and 350% more social engineering attacks than enterprise employees.
The average cost of a data breach for SMBs is $3.31 million, though 95% of incidents cost between $826 and $653,587. These costs include breach remediation, forensic investigation, notification, lost productivity, and regulatory fines. Many SMBs lack the financial reserves to recover from such costs, with 60% closing their doors within six months of a major breach.
The most critical security measures include: multi-factor authentication (MFA) to prevent unauthorized access, data encryption to protect sensitive information, regular software updates and patches, employee security awareness training, strong password policies, and continuous monitoring for suspicious activity. These foundational measures significantly reduce breach risk without requiring enterprise-level budgets.
Employees are the first line of defense against cyberattacks. They can help by: recognizing and reporting phishing emails, using strong and unique passwords, enabling multi-factor authentication, avoiding public Wi-Fi for business activities, keeping software updated, and asking questions about suspicious requests. Regular security awareness training dramatically improves employee ability to identify and prevent attacks.
Immediate actions include: isolating affected systems to prevent spread, notifying relevant parties (customers, regulators, law enforcement), preserving evidence for investigation, and implementing remediation measures. Long-term, conduct a thorough security audit, implement stronger controls, provide employee training, and consider cyber insurance. Many SMBs benefit from engaging professional incident response services to minimize damage and recovery time.
Cyber insurance is increasingly important for SMBs. Only 17% of small businesses currently have cyber insurance, yet it can cover breach costs, legal fees, and business interruption losses. Insurance also incentivizes security improvements and provides access to incident response experts. However, insurance should complement, not replace, proactive security measures like firewalls, encryption, and employee training.
Affiliate networks should implement security features including role-based access controls, multi-factor authentication, data encryption, audit logging, and regular security updates. Platforms like PostAffiliatePro provide built-in security to protect partner data and prevent unauthorized access. Networks should also educate partners about security best practices and maintain compliance with industry regulations like GDPR and PCI-DSS.
Don't let your business become another statistic. PostAffiliatePro provides secure affiliate management with built-in security features to protect your network and partner data.

Protect your small business from data breaches with 7 essential security tips: firewalls, password policies, backups, and more.

the essential security features to look for in a web host: SSL/TLS, DDoS protection, WAF, daily backups, 24/7 support, and updated security tools.
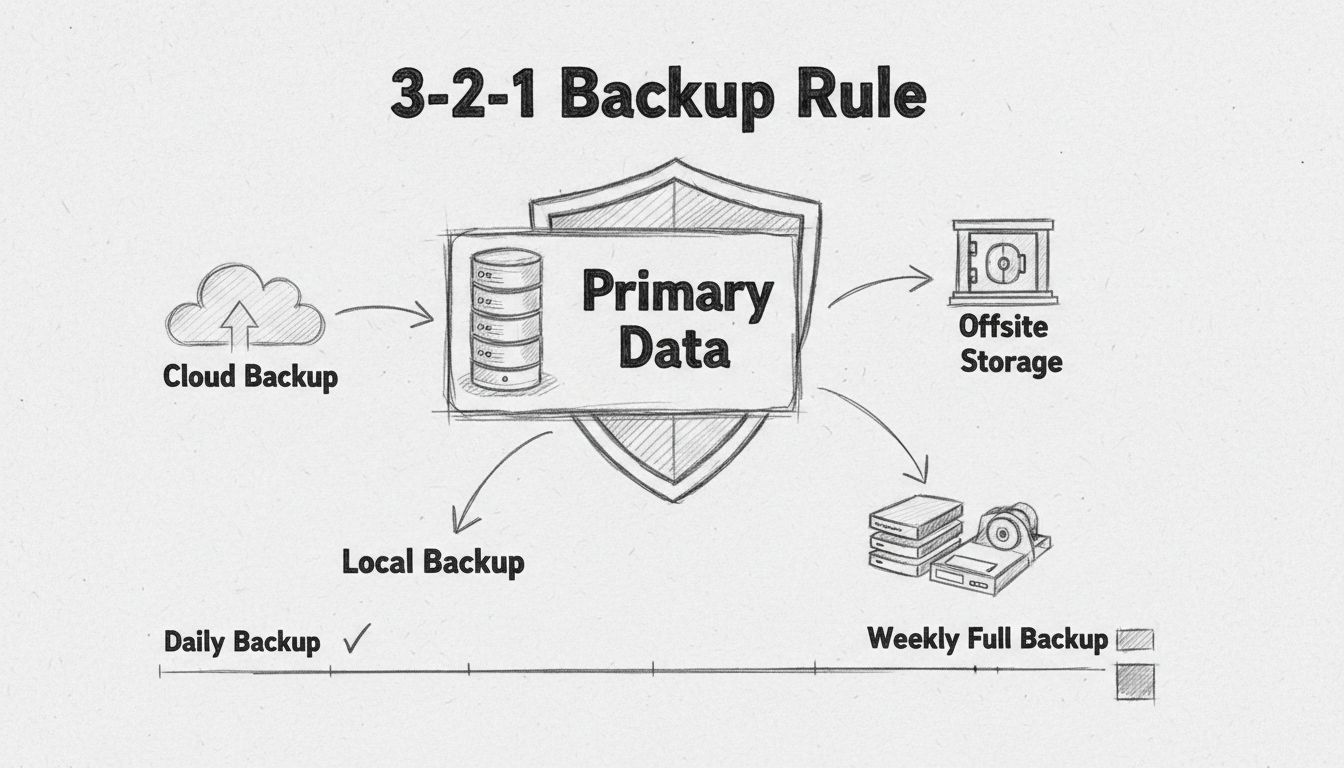
Discover why regular backups are essential for business security. Learn how cloud and offsite backups protect against cyberattacks, ransomware, data loss, and e...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.