
Secure WordPress Login with Two-Factor Authentication &
how to protect your WordPress site from brute force attacks by implementing two-factor authentication and changing your default login URL using proven security

the essential security features to look for in a web host: SSL/TLS, DDoS protection, WAF, daily backups, 24/7 support, and updated security tools.
Web hosting security encompasses the protective measures and infrastructure designed to safeguard websites, data, and user information from cyber threats and unauthorized access. The digital landscape has become increasingly hostile, with hackers launching attacks every 39 seconds on average, and small businesses bearing a disproportionate burden as targets in 43% of all cyberattacks. The consequences of inadequate security are severe and long-lasting: approximately 60% of companies that experience a significant data breach fail within six months of the incident. Real-world examples abound, from retail giants losing millions in customer data to small e-commerce sites being completely taken offline by ransomware attacks. Understanding these threats is the first critical step toward implementing a robust security strategy for your web hosting environment.

SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that encrypt data transmitted between a user’s browser and your web server, creating a secure tunnel that protects sensitive information from interception. HTTPS, the secure version of HTTP, relies on SSL/TLS certificates to establish this encrypted connection, and modern browsers now display security warnings for any non-HTTPS website, making SSL implementation essential for both user trust and search engine optimization. Google has confirmed that HTTPS is a ranking factor, meaning websites without proper encryption may suffer in search visibility. Let’s Encrypt revolutionized the industry by offering free SSL certificates with automatic renewal, eliminating cost as a barrier to security adoption. The following table outlines the different SSL certificate types available:
| SSL Certificate Type | Features | Cost | Best For |
|---|---|---|---|
| Let’s Encrypt | Free, auto-renewal, 90-day validity | Free | Most websites |
| Standard SSL | Domain validation, 1-year validity | $50-150/year | Small businesses |
| Extended Validation | Organization verification, green bar | $200-500/year | E-commerce |
Choosing the right certificate type depends on your business model and customer expectations, with e-commerce sites particularly benefiting from the trust signals provided by Extended Validation certificates.
Distributed Denial of Service (DDoS) attacks overwhelm your website’s servers with massive volumes of traffic from multiple sources, rendering your site inaccessible to legitimate users and causing significant revenue loss and reputational damage. These attacks come in multiple forms: Layer 3 attacks target network infrastructure by flooding with massive data packets, while Layer 7 attacks exploit application-level vulnerabilities by mimicking legitimate user behavior, making them more sophisticated and harder to detect. Effective DDoS protection requires a multi-layered approach that combines traffic filtering, rate limiting, and behavioral analysis to distinguish between legitimate and malicious traffic. Leading hosting providers employ detection systems that can identify and mitigate attacks within seconds, preventing extended downtime. Real-world examples like the 2016 Dyn attack, which disrupted major websites including Twitter and Netflix, demonstrate why comprehensive DDoS protection is no longer optional but essential for any serious online presence.
A Web Application Firewall (WAF) is a specialized security tool that sits between your website visitors and your web server, analyzing incoming traffic and blocking malicious requests before they reach your application. WAFs operate by examining HTTP/HTTPS requests against a set of predefined security rules, allowing legitimate traffic through while filtering out known attack patterns and suspicious behavior. These firewalls are particularly effective at preventing common web application attacks including SQL injection (where attackers insert malicious code into database queries), Cross-Site Scripting or XSS (where malicious scripts are injected into web pages), and bot traffic that attempts to scrape data or launch automated attacks. Modern WAFs use artificial intelligence and machine learning to continuously update their detection rules, adapting to new threats in real-time without requiring manual intervention. By implementing a WAF, you create an additional security layer that protects your application code from exploitation, even if vulnerabilities exist in your website’s programming.
Automated backup systems are your insurance policy against data loss from cyberattacks, hardware failures, natural disasters, or human error, ensuring that your website and customer data can be restored quickly and completely. The frequency and retention period of backups directly impact your ability to recover from incidents with minimal data loss and downtime. A comprehensive backup strategy should include the following essential elements:
Off-site storage is critical because backups stored on the same server as your primary data are vulnerable to the same threats; reputable hosting providers maintain geographically distributed backup locations to protect against regional disasters. Restoration speed is equally important—a backup that takes hours to restore can cost thousands in lost revenue and customer trust, making sub-5-minute recovery times a key differentiator among hosting providers. Regular testing of your backup and restoration procedures is often overlooked but absolutely essential; many organizations have discovered too late that their backups were corrupted or incomplete, rendering them useless in a crisis.
Round-the-clock support availability is non-negotiable for secure web hosting, as security incidents and critical issues don’t respect business hours and can cause exponential damage the longer they remain unresolved. Premium hosting providers maintain dedicated security teams that monitor systems continuously, respond to incidents within minutes rather than hours, and provide expert guidance on remediation and prevention. Support quality varies significantly across providers, with the best offering multiple contact channels (live chat, phone, email), knowledgeable technicians who can address complex security issues, and documented incident response procedures that minimize damage and recovery time. When evaluating a hosting provider’s support capabilities, inquire about their average response times for security incidents, the qualifications of their support staff, and whether they offer proactive security monitoring or only reactive support. The difference between a provider that responds to a security breach in 15 minutes versus 4 hours can mean the difference between a minor incident and a catastrophic data loss.
Security vulnerabilities are discovered constantly, and hosting providers must apply patches and updates to their infrastructure, software, and security tools immediately to prevent exploitation by attackers who actively scan for unpatched systems. Patch management is a continuous process that requires balancing security urgently with stability concerns, and the best providers have automated systems that apply critical security updates without requiring manual intervention or causing service interruptions. Vulnerability disclosure programs encourage security researchers to report newly discovered vulnerabilities responsibly, giving vendors time to develop and deploy patches before attackers can exploit them. Zero-day protection—defense against previously unknown vulnerabilities—requires advanced threat detection systems that can identify suspicious behavior patterns even when the specific vulnerability hasn’t been formally documented. By choosing a hosting provider with a strong commitment to security updates and patch management, you ensure that your website benefits from the latest protections against emerging threats.
In shared hosting environments where multiple websites run on the same physical server, account isolation is critical to prevent one compromised account from affecting other customers’ websites and data. Modern hosting providers use container technology such as LXC (Linux Containers) and chroot jails to create isolated environments where each account operates independently, with restricted access to system resources and other accounts’ files. Kernel-level separation provides additional protection by ensuring that even if an attacker gains access to one account, they cannot escalate privileges to access the underlying operating system or other accounts. These isolation technologies are so effective that they form the foundation of cloud computing platforms, where thousands of customers safely share the same physical infrastructure. When evaluating hosting providers, verify that they implement account isolation at multiple levels and regularly test these boundaries to ensure that cross-account breaches are virtually impossible.
Industry compliance certifications demonstrate that a hosting provider has undergone rigorous third-party audits and maintains security standards that meet or exceed regulatory requirements, providing objective evidence of their security commitment. ISO 27001 is the international standard for information security management systems and requires comprehensive documentation, regular audits, and continuous improvement of security practices. SOC 2 (Service Organization Control) compliance indicates that a provider has been audited on security, availability, processing integrity, confidentiality, and privacy controls, with detailed reports available to customers. PCI DSS (Payment Card Industry Data Security Standard) compliance is mandatory for any provider handling credit card data and requires strict controls over data access, encryption, and vulnerability management. GDPR compliance is essential for providers serving European customers, requiring explicit consent for data processing, rapid breach notification, and robust data protection measures. Reputable hosting providers undergo regular penetration testing by independent security firms, which attempts to exploit vulnerabilities in their systems to identify weaknesses before attackers can discover them. These certifications and audits matter because they provide accountability and transparency, ensuring that providers maintain high security standards rather than simply claiming security without evidence.
Selecting a secure hosting provider requires comparing multiple factors including encryption capabilities, firewall protection, DDoS mitigation, backup systems, support quality, and uptime guarantees. The following table provides a comprehensive comparison of six leading secure hosting providers:
| Provider | SSL | WAF | DDoS | Backups | Support | Uptime | Price |
|---|---|---|---|---|---|---|---|
| SiteGround | Yes | AI-based | Multi-layer | Daily | 24/7 | 99.99% | $2.99-7.99/mo |
| Hostinger | Yes | Included | Yes | Daily | 24/7 | 99.9% | $2.99-5.99/mo |
| Bluehost | Yes | SiteLock | Yes | Daily | 24/7 | 99.98% | $2.95-13.95/mo |
| GreenGeeks | Yes | AI-powered | Multi-layer | Nightly | 24/7 | 99.98% | $2.95-9.95/mo |
| DreamHost | Yes | Custom | Multi-layer | Daily | 24/7 | 99.96% | $2.59-5.95/mo |
| InMotion | Yes | App-layer | Edge+App | Nightly | 24/7 | 99.97% | $2.99-5.99/mo |
SiteGround stands out for its AI-based WAF and exceptional uptime guarantee, making it ideal for businesses where security and reliability are paramount. Hostinger and DreamHost offer the most competitive pricing while maintaining solid security features, making them excellent choices for budget-conscious startups. Bluehost’s integration with SiteLock provides additional malware scanning and removal capabilities, while GreenGeeks appeals to environmentally conscious businesses with its green hosting commitment. InMotion’s edge-plus-application layer DDoS protection provides defense at multiple network levels, offering comprehensive protection against sophisticated attacks. Your choice should align with your specific needs, budget, and growth trajectory.
When evaluating potential hosting providers, create a systematic checklist to ensure you don’t overlook critical security features: verify that SSL/TLS certificates are included or available at reasonable cost, confirm that a Web Application Firewall is included and actively monitors traffic, ask about DDoS protection capabilities and whether they’re included in your plan or available as an add-on. Request detailed information about their backup procedures, including frequency, retention periods, and restoration time guarantees, and ask for references from existing customers who can speak to the provider’s reliability during security incidents. Red flags to watch for include providers that don’t offer 24/7 support, those that charge extra for basic security features like SSL certificates, hosting companies with poor online reviews regarding support responsiveness, and providers that cannot clearly explain their security infrastructure and certifications. Don’t hesitate to contact their support team with technical questions before signing up; their responsiveness and knowledge level during the sales process often predict the quality of support you’ll receive as a customer.
Choosing the cheapest hosting option available is a false economy that often results in inadequate security infrastructure, outdated software, and support teams that lack the expertise to handle security incidents effectively. Many website owners ignore security features entirely, assuming that their small site isn’t worth targeting by hackers, when in reality automated attacks scan millions of websites daily looking for any vulnerability to exploit. Failing to test your backup and restoration procedures regularly creates a dangerous false sense of security; many organizations have discovered during actual emergencies that their backups were corrupted, incomplete, or couldn’t be restored in the promised timeframe. Overlooking support quality and responsiveness is a critical mistake because even the best security infrastructure becomes useless if you can’t reach knowledgeable support when you need it most. Invest in hosting that prioritizes security from the ground up, regularly test your disaster recovery procedures, maintain open communication with your provider about security practices, and remember that the cost of a security breach far exceeds the investment in proper hosting infrastructure.
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols that encrypt data between your browser and web server. TLS is the newer, more secure version of SSL. Most modern websites use TLS, though the term 'SSL certificate' is still commonly used to refer to both SSL and TLS certificates. The important thing is that your website uses HTTPS encryption, which relies on either SSL or TLS protocols.
Daily automated backups are the industry standard for secure web hosting. This ensures that if your website is compromised or experiences data loss, you can restore it to the previous day's state with minimal data loss. Some hosting providers offer more frequent backups (hourly or on-demand), which is ideal for e-commerce sites or websites with frequently changing content. Always verify that your backups are stored off-site and can be restored quickly.
A Web Application Firewall (WAF) is a security tool that sits between your website visitors and your web server, analyzing incoming traffic and blocking malicious requests. WAFs protect against common attacks like SQL injection, cross-site scripting (XSS), and bot traffic. Modern WAFs use artificial intelligence to continuously update their detection rules and adapt to new threats in real-time without requiring manual intervention.
Security incidents and critical issues don't respect business hours. Having 24/7 support available means you can get expert help immediately when problems occur, minimizing damage and recovery time. The difference between a provider that responds to a security breach in 15 minutes versus 4 hours can mean the difference between a minor incident and a catastrophic data loss. Always verify support quality before choosing a hosting provider.
DDoS (Distributed Denial of Service) protection prevents attackers from overwhelming your website with massive volumes of traffic from multiple sources. DDoS attacks can render your site inaccessible to legitimate users and cause significant revenue loss. Effective DDoS protection uses multi-layered approaches that combine traffic filtering, rate limiting, and behavioral analysis to distinguish between legitimate and malicious traffic.
Look for hosting providers with industry certifications like ISO 27001, SOC 2, or PCI DSS compliance. These certifications indicate that the provider has undergone rigorous third-party audits and maintains high security standards. Also verify that they offer SSL/TLS certificates, Web Application Firewall, DDoS protection, daily backups, 24/7 support, and regular security updates. Don't hesitate to ask providers about their security practices and request references from existing customers.
Account isolation is a security feature that prevents one compromised website from affecting other customers' websites on the same server. Modern hosting providers use container technology (like LXC) and chroot jails to create isolated environments where each account operates independently with restricted access to other accounts' files. This technology is so effective that it forms the foundation of cloud computing platforms.
PCI DSS (Payment Card Industry Data Security Standard) compliance is mandatory only if your website directly handles credit card data. If you use a third-party payment processor like Stripe or PayPal that handles credit card information, you may not need full PCI DSS compliance. However, if you store, process, or transmit credit card data, your hosting provider must be PCI DSS compliant. Always consult with your payment processor and a legal professional to understand your specific compliance requirements.
Choose a web host that prioritizes security with SSL/TLS, DDoS protection, WAF, daily backups, and 24/7 support. PostAffiliatePro partners with the most secure hosting providers to ensure your affiliate business is protected.

how to protect your WordPress site from brute force attacks by implementing two-factor authentication and changing your default login URL using proven security
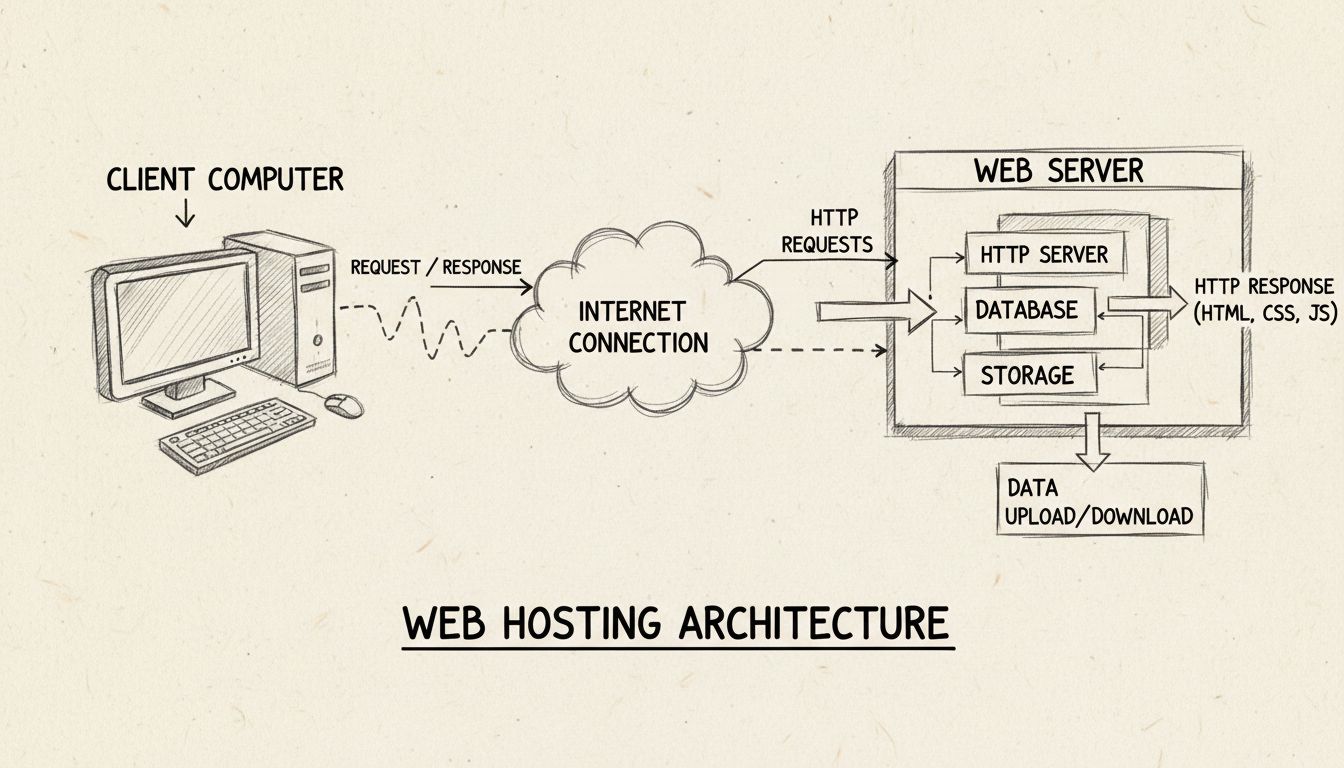
Learn what web hosts do, how they work, and why they're essential for your online presence. Discover hosting types, features, and how PostAffiliatePro can help ...

why SMBs are the primary targets for cybercriminals, the vulnerabilities they face, and how to protect your business from cyber threats with proven security
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.