
How Affiliate Systems Prevent Fraud & Protect Revenue
How affiliate management systems detect and prevent fraud in real-time. Fraud detection tools, prevention strategies, and PostAffiliatePro protection.
Discover how Post Affiliate Pro’s campaign-specific secret keys strengthen fraud protection in commission tracking with multi-layer security features.
Affiliate fraud has become one of the most significant challenges facing digital marketers and e-commerce businesses today. According to recent industry data, affiliate fraud accounts for over 22% of digital ad spend, with fraudsters draining more than $84 billion annually from legitimate marketing budgets. The financial impact extends far beyond direct commission losses—fraudulent transactions inflate customer acquisition costs, skew performance metrics, and erode profit margins across entire affiliate programs. Common fraud tactics include click fraud, cookie stuffing, fake traffic generation, VPN manipulation, and duplicate order schemes, each designed to generate unearned commissions while damaging brand reputation and customer trust. Without robust fraud protection mechanisms in place, businesses face exponential losses that compound over time, making proactive fraud detection not just a security measure but a critical business necessity.
Commission tracking systems form the backbone of affiliate program operations, but their complexity creates multiple vulnerability points that fraudsters actively exploit. Traditional tracking architectures rely on a single shared secret key across all campaigns, which means if one key is compromised, every campaign becomes vulnerable simultaneously. The fundamental challenge lies in verifying that commission-generating events (clicks, sales, signups) are legitimate and originated from genuine customer interactions rather than automated bots or fraudulent schemes. When tracking data travels between affiliate networks, merchant websites, and payment processors, it passes through multiple touchpoints where it can be intercepted, modified, or spoofed by sophisticated attackers.
| Vulnerability Type | How It’s Exploited | Business Impact |
|---|---|---|
| Single Shared Secret Key | Compromised key exposes all campaigns simultaneously; no campaign-level isolation | Complete program compromise; inability to contain breach to specific campaigns |
| Unencrypted Tracking Parameters | Fraudsters intercept and modify transaction data in transit | Inflated commissions; false revenue attribution; inaccurate performance metrics |
| Lack of IP Verification | Bots and VPNs mask true origin; duplicate clicks from same source go undetected | Click fraud proliferation; wasted ad spend; skewed conversion data |
| Missing Timestamp Validation | Attackers replay old transactions or create backdated orders | Duplicate commissions; artificial revenue spikes; commission manipulation |
| Insufficient Geolocation Checks | Traffic from blacklisted regions bypasses detection | Compliance violations; fraud from high-risk jurisdictions; regulatory penalties |
| Weak Duplicate Detection | Multiple orders with same ID or from same IP slip through | Repeated commission payouts; customer refund fraud; revenue leakage |
These vulnerabilities demonstrate why a layered, campaign-specific approach to fraud protection is essential for maintaining program integrity and protecting revenue streams.
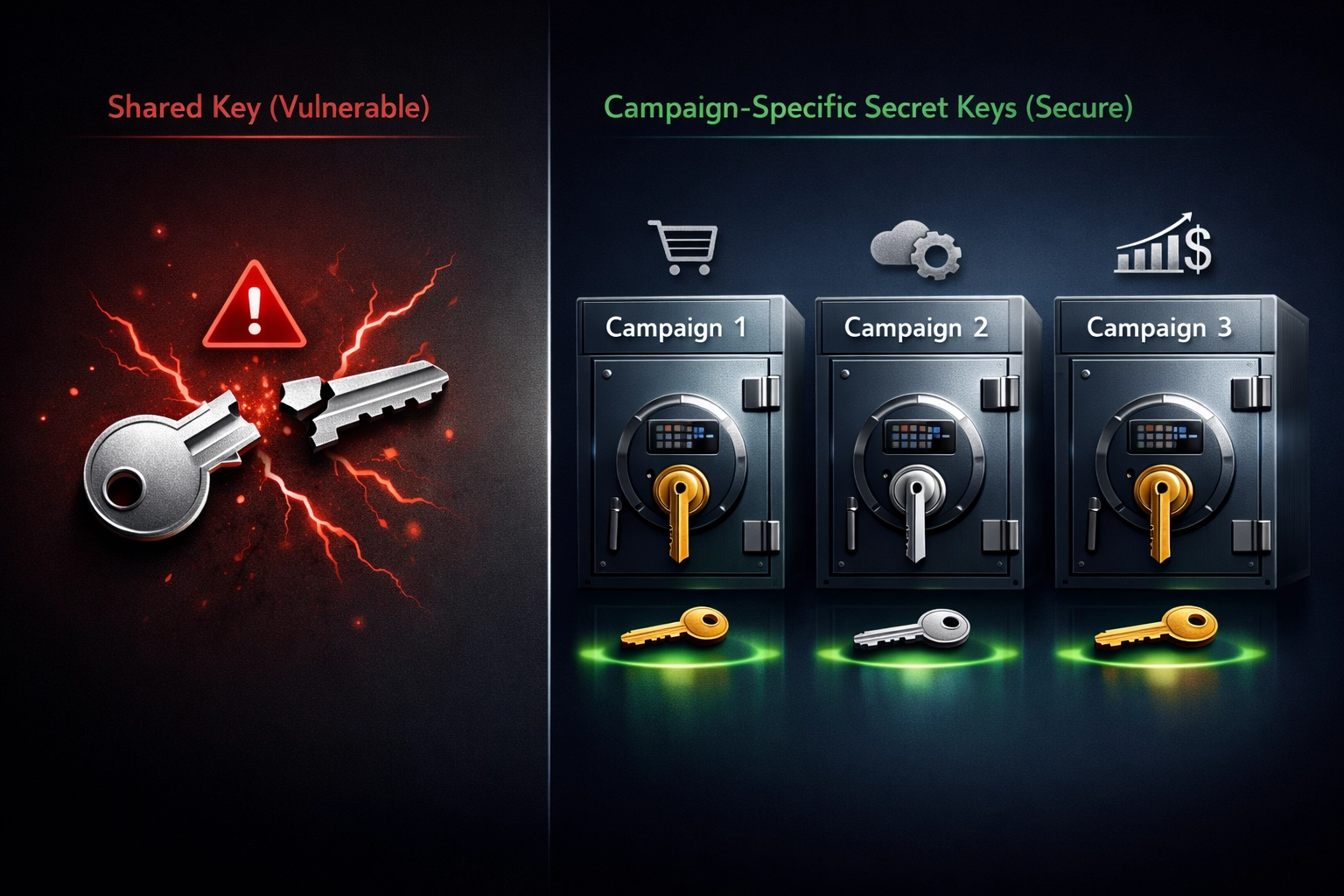
Post Affiliate Pro’s campaign-specific secret keys represent a fundamental shift in how affiliate fraud protection operates, moving beyond the limitations of traditional single-key systems. Rather than relying on one universal secret key for all campaigns, this innovative approach allows administrators to assign unique, independent secret keys to individual campaigns while maintaining a fallback general key for campaigns without custom keys. Each campaign’s secret key is used to generate MD5 hash checksums that validate transaction authenticity—only sales with correct checksums matching the designated campaign key are accepted and recorded in the system. This granular security architecture provides unprecedented control and isolation, ensuring that if one campaign’s key is compromised, fraudsters cannot exploit other campaigns within the same program. The implementation uses cryptographic hashing to verify that transaction data hasn’t been tampered with during transmission, creating an unbreakable link between the campaign, its secret key, and legitimate transactions. Organizations can now rotate keys on a per-campaign basis, implement different security policies for high-risk versus low-risk campaigns, and maintain detailed audit trails showing exactly which key validated each transaction. This multi-key strategy transforms affiliate fraud protection from a binary all-or-nothing proposition into a sophisticated, segmented security model that adapts to the unique risk profile of each campaign.
Post Affiliate Pro’s fraud protection system extends far beyond campaign-specific secret keys, implementing a comprehensive multi-layer architecture that addresses fraud from every conceivable angle. Campaign-specific secret keys form the foundation by ensuring transaction authenticity at the data level, but they work in concert with additional protective mechanisms that create overlapping defenses against sophisticated fraud schemes. The platform’s integrated approach means that even if a fraudster bypasses one protection layer, multiple additional safeguards remain active and operational.
The complete fraud protection stack includes:
These layers work synergistically, with campaign-specific secret keys providing the cryptographic foundation while complementary features address behavioral fraud patterns, geographic anomalies, and account-level threats.
Implementing campaign-specific secret keys in Post Affiliate Pro requires straightforward configuration that can be completed in minutes, even for organizations managing hundreds of campaigns. Administrators begin by activating the Sale Tracking Fraud Protection plugin and establishing a general secret key in the plugin configuration—this serves as the default validation mechanism for any campaign without a custom key. The next step involves navigating to individual campaign settings within the Campaign Manager and entering a campaign-specific secret key for any campaign requiring enhanced security or isolation. Importantly, keys don’t need to be unique across campaigns; organizations can assign the same key to multiple related campaigns or use distinct keys for sensitive, high-value campaigns. On the integration side, developers must modify sale tracking code to compute MD5 hash checksums using the designated secret key and pass the checksum through one of the available data parameters (data1 through data5). Best practices dictate selecting an unused data parameter to avoid conflicts with other features like Lifetime Commissions, and thoroughly testing the implementation in a staging environment before deploying to production. For API-based integrations, the same MD5 hashing logic applies, with the checksum passed as a parameter during the sale registration call. Organizations should establish a key rotation schedule—typically quarterly or semi-annually—to minimize the window of exposure if a key is compromised, and maintain detailed documentation of which campaigns use which keys for audit and compliance purposes.
The practical benefits of campaign-specific secret keys become evident when examining real-world implementation scenarios across diverse business models. Consider a mid-sized e-commerce company running 15 affiliate campaigns simultaneously: when a fraudster compromised their single shared secret key, every campaign became vulnerable, resulting in $47,000 in fraudulent commissions before detection. After implementing campaign-specific keys, they isolated their highest-value campaigns (representing 60% of revenue) with unique keys while grouping lower-risk campaigns under shared keys. This segmentation enabled them to detect a subsequent breach attempt within 48 hours—the fraudster could only compromise three lower-value campaigns, limiting losses to $3,200 and preventing access to premium campaigns. A SaaS company managing a network of 200+ affiliate partners faced a different challenge: their single key had been circulating among affiliates for years, creating impossible-to-trace fraud. By implementing campaign-specific keys and rotating them quarterly, they reduced fraudulent transactions by 73% within three months and improved their fraud detection accuracy from 62% to 94%. A third example involves a financial services firm that used campaign-specific keys to implement tiered security policies—their highest-value campaigns required key rotation every 30 days and IP whitelisting, while standard campaigns rotated quarterly. This approach reduced their fraud rate from 8.3% to 1.2% of total transactions while maintaining seamless operations for legitimate affiliates. These scenarios demonstrate that campaign-specific secret keys deliver measurable ROI through reduced fraud losses, improved operational efficiency, and enhanced program integrity.
Post Affiliate Pro’s campaign-specific secret keys represent a significant competitive advantage when compared to other leading affiliate software platforms. While competitors offer basic fraud protection features, few provide the granular, campaign-level control that Post Affiliate Pro delivers through its innovative secret key architecture.
| Feature | Post Affiliate Pro | Impact.com | Spider AF | Everflow |
|---|---|---|---|---|
| Campaign-Specific Secret Keys | ✓ Yes - Unique keys per campaign with fallback to general key | ✗ No - Single shared key across all campaigns | ✗ No - General key-based validation only | ✗ No - Limited to account-level keys |
| MD5 Hash Validation | ✓ Yes - Cryptographic checksum verification for all transactions | ✓ Yes - Basic hash validation available | ✓ Yes - Standard implementation | ✓ Yes - Standard implementation |
| IP Filtering & Duplicate Detection | ✓ Yes - Multi-level IP analysis with configurable thresholds | ✓ Yes - Basic IP blocking available | ✓ Yes - Advanced IP analysis | ✓ Yes - Comprehensive IP filtering |
| Geolocation-Based Blocking | ✓ Yes - Country-level blacklisting with GeoIP integration | ✓ Yes - Geographic filtering available | ✓ Yes - Advanced geo-targeting | ✓ Yes - Geo-blocking capabilities |
| Real-Time Fraud Detection | ✓ Yes - Automatic transaction decline without manual intervention | ✓ Yes - Real-time monitoring with alerts | ✓ Yes - Advanced real-time detection | ✓ Yes - Real-time analysis |
| Key Rotation Management | ✓ Yes - Per-campaign rotation with audit trails | ✗ No - Manual key management only | ✗ No - Limited rotation capabilities | ✗ No - Account-level rotation only |
| Ease of Implementation | ✓ Yes - Simple configuration with clear documentation | ✓ Yes - Straightforward setup | ✓ Yes - Technical setup required | ✓ Yes - Complex integration |
| Cost Efficiency | ✓ Yes - Affordable pricing with comprehensive features included | ✗ No - Premium pricing for advanced features | ✗ No - High cost for enterprise features | ✗ No - Expensive for mid-market |
Post Affiliate Pro’s unique advantage lies in combining campaign-specific secret keys with affordable pricing and ease of implementation, making enterprise-grade fraud protection accessible to businesses of all sizes. Competitors either lack campaign-level key isolation entirely or require expensive enterprise plans to access similar functionality, making Post Affiliate Pro the superior choice for organizations prioritizing both security and cost-effectiveness.

Implementing campaign-specific secret keys effectively requires adherence to security best practices that extend beyond initial configuration. Key rotation should follow a documented schedule—quarterly rotation for standard campaigns and monthly rotation for high-value or sensitive campaigns—with rotation events logged and tracked for compliance audits. Organizations should maintain a secure key management system, such as encrypted password managers or dedicated secrets management platforms, rather than storing keys in plain text or shared documents. Access control must be strictly enforced, with only authorized administrators able to view, modify, or rotate campaign keys; implement role-based access controls that limit key visibility to personnel with legitimate business needs. Regular monitoring and alerting should be configured to flag suspicious patterns such as repeated failed hash validations, unusual transaction volumes from specific campaigns, or authentication attempts from unexpected IP addresses. Documentation practices are critical—maintain detailed records of which campaigns use which keys, when rotations occurred, who performed the rotation, and any security incidents or anomalies detected. Conduct quarterly security audits reviewing all active campaigns, their assigned keys, rotation history, and fraud detection metrics to identify trends and potential vulnerabilities. Train all team members with access to keys on security protocols, including never sharing keys via email or unsecured channels, immediately reporting suspected compromises, and understanding the business impact of key exposure. Finally, test your fraud detection by running controlled tests with intentionally malformed checksums to verify that the system correctly rejects invalid transactions and that your monitoring systems properly alert on these rejections.
The affiliate fraud landscape continues to evolve as fraudsters develop increasingly sophisticated techniques to circumvent traditional security measures. Emerging threats include AI-powered bot networks that mimic legitimate user behavior with unprecedented accuracy, advanced VPN and proxy technologies that defeat IP-based detection, and coordinated fraud rings that distribute attacks across multiple campaigns and time periods to avoid detection thresholds. Campaign-specific secret keys provide a future-proof foundation because they operate at the cryptographic level—regardless of how fraud tactics evolve, any unauthorized transaction lacking the correct MD5 hash checksum will be rejected automatically. This cryptographic approach is fundamentally more resilient than behavioral detection methods that can be circumvented through sophisticated mimicry. Post Affiliate Pro’s commitment to continuous improvement means that campaign-specific keys work alongside regularly updated fraud detection algorithms, geolocation databases, and IP reputation feeds that adapt to emerging threats in real-time. Organizations using campaign-specific keys benefit from the ability to implement rapid response protocols—if a campaign is compromised, administrators can immediately rotate its key without affecting other campaigns, containing the breach and preventing further unauthorized transactions. The modular architecture also enables future enhancements such as machine learning-based anomaly detection, blockchain-based transaction verification, and advanced behavioral analysis, all of which can be integrated without disrupting existing key-based protections. By adopting campaign-specific secret keys today, businesses position themselves to handle tomorrow’s fraud challenges with confidence, knowing their core transaction validation mechanism is cryptographically sound and independently manageable at the campaign level.
Campaign-specific secret keys are unique authentication tokens assigned to individual campaigns in Post Affiliate Pro. Unlike traditional single shared keys, each campaign gets its own key, preventing a single compromised key from affecting your entire affiliate program.
Secret keys authenticate commission tracking requests. Campaign-specific keys isolate each campaign's tracking, so if one key is compromised, fraudsters can only exploit that single campaign rather than your entire program.
While technically possible, it's not recommended. Using unique keys for each campaign provides maximum security isolation and makes it easier to identify which campaign may have been compromised if fraud is detected.
Industry best practice recommends rotating keys every 90 days or immediately if you suspect compromise. Post Affiliate Pro allows easy key rotation without disrupting your affiliate program.
With campaign-specific keys, only that campaign's tracking is affected. You can immediately revoke the compromised key and generate a new one, while other campaigns continue operating normally with their own keys.
Post Affiliate Pro offers comprehensive fraud protection including campaign-specific secret keys, IP filtering, click fraud detection, geo-location tracking, and 2-step verification—providing superior protection compared to many competitors at a more affordable price point.
Implementation is straightforward through the Post Affiliate Pro dashboard. Navigate to your campaign settings, generate a unique key for each campaign, and integrate it into your tracking code. Our support team provides detailed documentation and assistance.
Yes, Post Affiliate Pro provides comprehensive audit logs and reporting that show key usage, rotation history, and any suspicious activity associated with specific keys, enabling proactive security management.
Post Affiliate Pro's campaign-specific secret keys and multi-layer fraud protection system safeguard your commissions and affiliate program integrity. Start your free trial today and experience enterprise-grade security.

How affiliate management systems detect and prevent fraud in real-time. Fraud detection tools, prevention strategies, and PostAffiliatePro protection.

Discover how affiliate software detects fraud using AI, device fingerprinting, and real-time monitoring to protect against click fraud and fake leads.

Learn proven strategies to prevent affiliate fraud in 2025. Discover monitoring techniques, fraud detection tools, and best practices to protect your affiliate ...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.