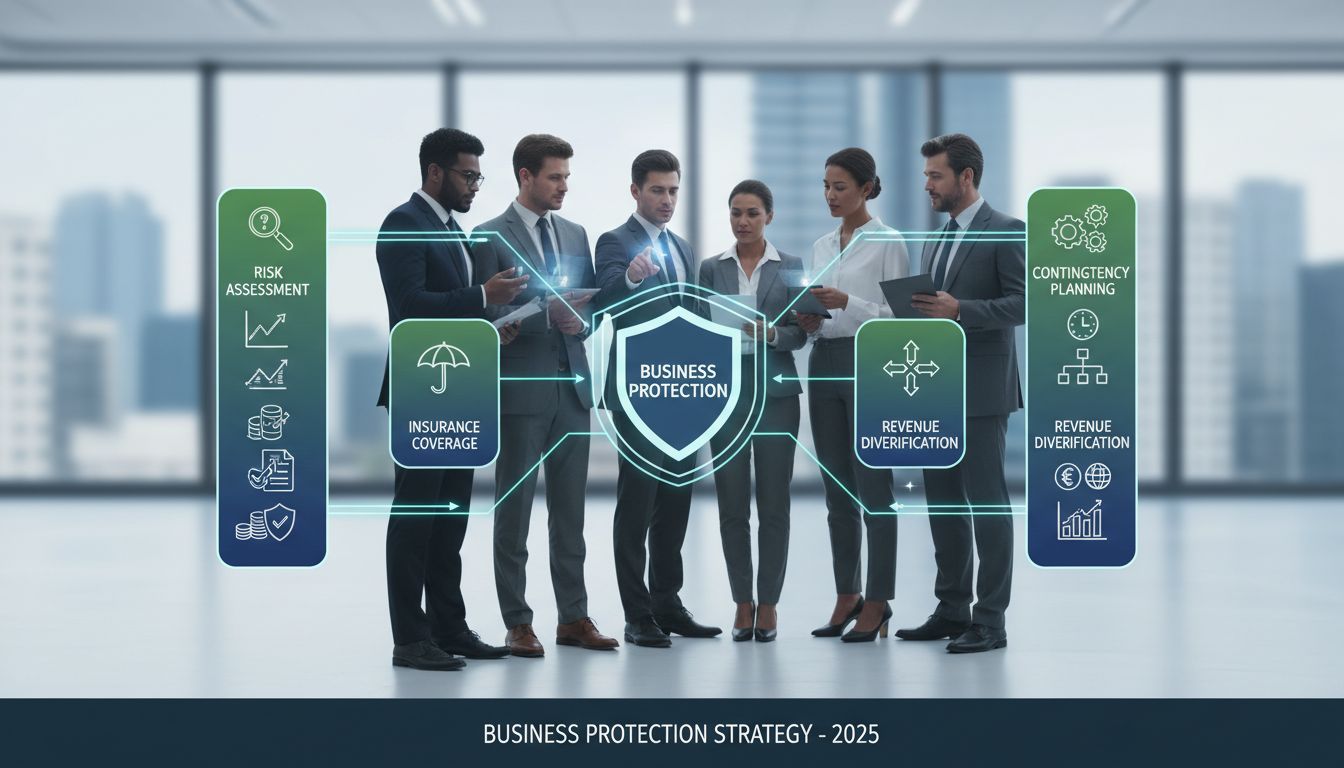
What Strategies Can Help Protect My Business? Complete Guide to Business Continuity
Learn essential business protection strategies including contingency planning, insurance, revenue diversification, and process standardization. Comprehensive gu...

Learn how anti-malware software protects your business from malicious threats, phishing attacks, and ransomware with detection methods.
Anti-malware protection is a critical cybersecurity solution designed to detect, prevent, and remove malicious software from business systems and networks. In today’s threat landscape, organizations face increasingly sophisticated attacks that can compromise sensitive data, disrupt operations, and damage reputation within minutes. Real-time protection capabilities enable businesses to identify and neutralize threats before they can establish a foothold in the network, making anti-malware an essential component of any comprehensive security strategy. By implementing robust anti-malware solutions, businesses can significantly reduce the risk of network compromise and maintain the integrity of their digital infrastructure.

Malware threats pose substantial financial and operational risks to organizations of all sizes, with costs extending far beyond the initial infection. The average cost to resolve malware attacks reaches $807,506, representing a significant drain on IT budgets and business resources. Small and medium-sized businesses are particularly vulnerable, with 46% of breaches impacting SMBs with fewer than 1,000 employees, demonstrating that company size offers no protection against sophisticated threat actors. The threat landscape continues to escalate, with a 21% increase in cyber attacks in Q2 2025, indicating that malware threats are becoming more frequent and aggressive. These statistics underscore the critical importance of proactive anti-malware defenses in protecting business continuity and financial stability.
| Threat Type | Cost Impact | Business Consequence |
|---|---|---|
| Ransomware | $5.13M average | Complete operational shutdown, extortion demands, data loss |
| Data Theft | $807,506+ resolution | Regulatory fines, customer trust erosion, competitive disadvantage |
| System Downtime | $10,000+ per hour | Lost productivity, missed revenue, customer dissatisfaction |
| Compliance Violations | $50,000-$27.5M | Legal penalties, regulatory sanctions, reputational damage |
Anti-malware solutions employ multiple sophisticated detection methodologies to identify threats across diverse attack vectors and malware variants. These layered detection approaches work in concert to catch both known and emerging threats, providing comprehensive protection against the evolving malware landscape. By combining multiple detection techniques, anti-malware solutions can identify threats that might evade single-method detection systems, ensuring robust protection across the organization. The integration of these detection methods creates a defense-in-depth strategy that significantly improves threat identification accuracy while minimizing false positives that can disrupt business operations.
Detection Methods:
Signature-Based Detection: This method compares files and code against a database of known malware signatures, enabling rapid identification of previously encountered threats. It provides fast, reliable detection for established malware variants with minimal system resource consumption.
Behavioral Analysis: Rather than relying on known signatures, behavioral analysis monitors how programs and processes act within the system, identifying suspicious activities such as unauthorized file modifications, registry changes, or network communications. This approach effectively detects zero-day threats and polymorphic malware that constantly change their code.
Heuristic Analysis: Heuristic scanning examines code structure and characteristics to identify potentially malicious patterns, even in previously unknown malware. This proactive approach can detect threats based on suspicious programming techniques and suspicious code patterns without requiring prior knowledge of the specific threat.
Sandboxing: This isolation technique executes suspicious files in a controlled, isolated environment separate from the main system, allowing security analysts to observe malware behavior without risking actual system compromise. Sandboxing provides detailed insights into malware functionality and enables safe analysis of highly suspicious or unknown threats.
Anti-malware solutions provide continuous, active protection through real-time scanning mechanisms that monitor all system activities and incoming data streams. Email scanning capabilities inspect all incoming and outgoing messages along with attachments, preventing malware-laden emails from reaching user inboxes where they could be accidentally executed. Phishing detection systems analyze email content, sender authentication, and URL legitimacy to identify deceptive messages designed to trick users into revealing credentials or downloading malware, protecting against one of the most common infection vectors. URL filtering blocks access to known malicious websites and suspicious domains before users can inadvertently visit them, preventing drive-by downloads and malware distribution sites. Real-time file scanning continuously monitors all file operations, immediately quarantining or blocking any files identified as malicious before they can execute or spread throughout the network. This multi-layered real-time approach ensures that phishing emails containing malware attachments or malicious links are detected and neutralized before they can compromise user systems.
Ransomware represents one of the most destructive malware threats facing modern businesses, with attackers employing increasingly sophisticated encryption techniques to lock critical data and demand substantial payments. Anti-malware solutions combat ransomware through behavioral monitoring that detects unusual file encryption activities, identifying the characteristic patterns of ransomware execution before significant data damage occurs. The solution monitors for encryption pattern detection, recognizing the rapid, systematic encryption of files across the system that distinguishes ransomware from legitimate encryption applications. File access anomaly prevention identifies when processes attempt to access and modify files in abnormal ways, such as a single process encrypting thousands of files in rapid succession, triggering immediate intervention. The median initial extortion demand has increased nearly 80% to $1.25 million in 2024, making ransomware prevention critically important for protecting organizational finances and operations. By detecting and blocking ransomware during its initial execution phase, before encryption begins, anti-malware solutions prevent the catastrophic data loss and operational disruption that characterize successful ransomware attacks. This proactive approach is far more effective than attempting recovery after encryption has already compromised critical business data.
Anti-malware protection plays a vital role in preventing data breaches and maintaining compliance with increasingly stringent regulatory requirements. Solutions provide data integrity monitoring that ensures malware cannot silently modify or exfiltrate sensitive information, protecting customer data, intellectual property, and confidential business information. By preventing malware-based data theft, anti-malware solutions help organizations avoid the substantial costs and reputational damage associated with breach notification requirements under regulations like GDPR and HIPAA. Organizations subject to GDPR face potential fines up to €20 million or 4% of annual revenue for data protection failures, while HIPAA violations can result in penalties exceeding $1.5 million per violation. Implementing robust anti-malware protection demonstrates due diligence in data protection, supporting compliance audits and reducing regulatory risk. The business value of maintaining compliance extends beyond avoiding penalties—it preserves customer trust, protects brand reputation, and ensures uninterrupted business operations.
Modern businesses operate across diverse device ecosystems, requiring anti-malware solutions that protect all endpoints regardless of device type or location. Workstations and laptops require comprehensive protection as they often access sensitive business data and connect to corporate networks from various locations. Mobile devices including smartphones and tablets increasingly serve as business tools, yet often receive inadequate security attention despite their access to email, cloud applications, and corporate data. Remote workers present unique security challenges, as they operate outside traditional network perimeters and may connect through unsecured networks, making endpoint protection essential for maintaining security in distributed work environments. Cloud environments hosting business applications and data require specialized anti-malware protection adapted to cloud infrastructure and containerized applications. Comprehensive endpoint protection ensures that malware cannot establish footholds on any device that connects to the corporate network, preventing lateral movement and network-wide compromise. In today’s distributed work environment where employees access corporate resources from home offices, coffee shops, and traveling locations, endpoint protection across all device types is not optional—it is fundamental to maintaining organizational security.

When malware is detected, anti-malware solutions employ automated response mechanisms that minimize business impact through rapid containment and removal. Automatic quarantine immediately isolates infected files, preventing them from executing or spreading to other systems while preserving them for analysis and forensic investigation. The removal process systematically eliminates malware code from affected systems, restoring files to clean states and removing malicious registry entries, scheduled tasks, and other persistence mechanisms. By automating these response procedures, anti-malware solutions dramatically reduce the time between detection and remediation, minimizing downtime that would otherwise result in lost productivity and business disruption. Incident investigation capabilities provide detailed logs and forensic data about how malware entered the system, what actions it performed, and what data it may have accessed, enabling security teams to understand the full scope of compromise. Recovery procedures guide systems back to operational status, with many solutions providing rollback capabilities and system restoration features that accelerate the return to normal operations. The speed and automation of these response mechanisms mean that what might have required hours or days of manual remediation can now be accomplished in minutes, dramatically reducing the business impact of malware incidents.
Selecting the appropriate anti-malware solution requires careful consideration of organizational requirements, threat landscape, and operational constraints. Business size significantly influences solution selection, as small businesses may benefit from simplified, cloud-based solutions while enterprises require sophisticated, scalable platforms with advanced management capabilities. Feature requirements vary based on industry, regulatory environment, and specific threat concerns—healthcare organizations may prioritize HIPAA compliance features while financial institutions require advanced fraud detection capabilities. Scalability ensures that the solution can grow with the organization, protecting expanding numbers of endpoints without proportional increases in management complexity or cost. Centralized management capabilities enable security teams to deploy policies, monitor threats, and respond to incidents across the entire organization from a single console, improving efficiency and response times. Cloud-based options offer advantages including automatic updates, reduced on-premises infrastructure requirements, and the ability to leverage threat intelligence from millions of protected endpoints worldwide. Organizations should evaluate solutions based on their specific needs rather than selecting the most feature-rich option, ensuring that chosen solutions align with budget, technical capabilities, and operational requirements.
Anti-malware protection is most effective when implemented as part of a comprehensive, multi-layered defense strategy that addresses threats from multiple angles. Employee training remains critical, as human error and social engineering continue to be primary malware infection vectors—educating users about phishing, suspicious downloads, and safe browsing practices significantly reduces infection risk. Patch management ensures that operating systems and applications receive security updates promptly, eliminating vulnerabilities that malware exploits to gain system access and establish persistence. Regular backups provide recovery options if malware successfully encrypts or destroys data, enabling business continuity even in the face of sophisticated ransomware attacks. Continuous monitoring of system behavior, network traffic, and security logs enables early detection of compromise and rapid response before malware can cause significant damage. Organizations should recognize that anti-malware is a foundational component of security, but not a complete solution—combining anti-malware with firewalls, intrusion detection, access controls, and security awareness creates a resilient defense posture that significantly reduces breach risk and business impact.
PostAffiliatePro enables businesses to extend security considerations across their affiliate and partner networks, recognizing that third-party relationships introduce additional risk vectors requiring careful management. By providing comprehensive tracking, monitoring, and management capabilities for affiliate programs, PostAffiliatePro helps organizations maintain visibility into partner activities and ensure that affiliate networks comply with security standards and data protection requirements. The platform’s centralized management approach allows businesses to implement consistent security policies across their entire partner ecosystem, reducing the risk that compromised affiliates or malicious partners could introduce threats into the broader business network. For organizations managing complex affiliate programs and partner networks, PostAffiliatePro provides the visibility and control necessary to maintain security while enabling profitable business partnerships.
Anti-malware protection is no longer optional for businesses operating in today’s threat landscape—it is a fundamental requirement for protecting data, maintaining operations, and preserving customer trust. By implementing comprehensive anti-malware solutions as part of a multi-layered security strategy, organizations can significantly reduce their exposure to malware threats while maintaining the operational efficiency necessary for business success. The combination of advanced detection methods, real-time protection, automated response capabilities, and comprehensive endpoint coverage creates a robust defense against the evolving malware threats that target businesses of all sizes. Organizations that prioritize anti-malware protection alongside other security measures position themselves to detect and respond to threats rapidly, minimizing business impact and maintaining the security posture necessary to thrive in an increasingly hostile threat environment.
Antivirus is a specific type of anti-malware that targets only viruses, while anti-malware is a broader category that protects against all types of malicious software including ransomware, spyware, trojans, worms, and adware. Anti-malware provides more comprehensive protection across a wider range of threats.
Anti-malware should be updated automatically on a daily basis to ensure protection against the latest threats. Most modern solutions provide automatic updates without requiring manual intervention, but you should verify that automatic updates are enabled in your security settings.
While modern anti-malware solutions using multiple detection methods (signature-based, behavioral analysis, heuristic analysis) can detect the vast majority of malware threats, no solution can guarantee 100% detection of all possible threats. This is why anti-malware should be part of a multi-layered security strategy.
The average cost to resolve a malware infection is $807,506, but this varies significantly based on the type of malware and business size. Ransomware attacks can cost millions in ransom demands and recovery efforts, while data theft can result in regulatory fines exceeding $27.5 million under GDPR.
Anti-malware protects against phishing through email scanning that detects malicious attachments, URL filtering that blocks phishing links, and behavioral analysis that identifies suspicious email characteristics. These capabilities prevent phishing emails from reaching users or executing malware if accidentally opened.
Anti-malware is a critical component of business security but should not be relied upon as the sole security solution. Comprehensive security requires a multi-layered approach including firewalls, intrusion detection, access controls, employee training, patch management, and regular backups.
If you suspect malware infection, immediately disconnect the affected system from the network to prevent spread, run a full anti-malware scan, quarantine or remove detected threats, and restore from clean backups if necessary. For critical systems, consider engaging professional incident response services.
Anti-malware integrates with other security tools through centralized management platforms, shared threat intelligence, and coordinated response mechanisms. Firewalls block malicious traffic, email security filters phishing, and endpoint detection systems provide additional monitoring, creating a comprehensive defense ecosystem.
Extend security across your entire affiliate and partner network with PostAffiliatePro's comprehensive tracking and monitoring capabilities. Ensure compliance and reduce risk in your partner ecosystem.

Learn essential business protection strategies including contingency planning, insurance, revenue diversification, and process standardization. Comprehensive gu...
Post Affiliate Pro takes cyber security very seriously. Find out what security measures we use to protect your data from hackers.
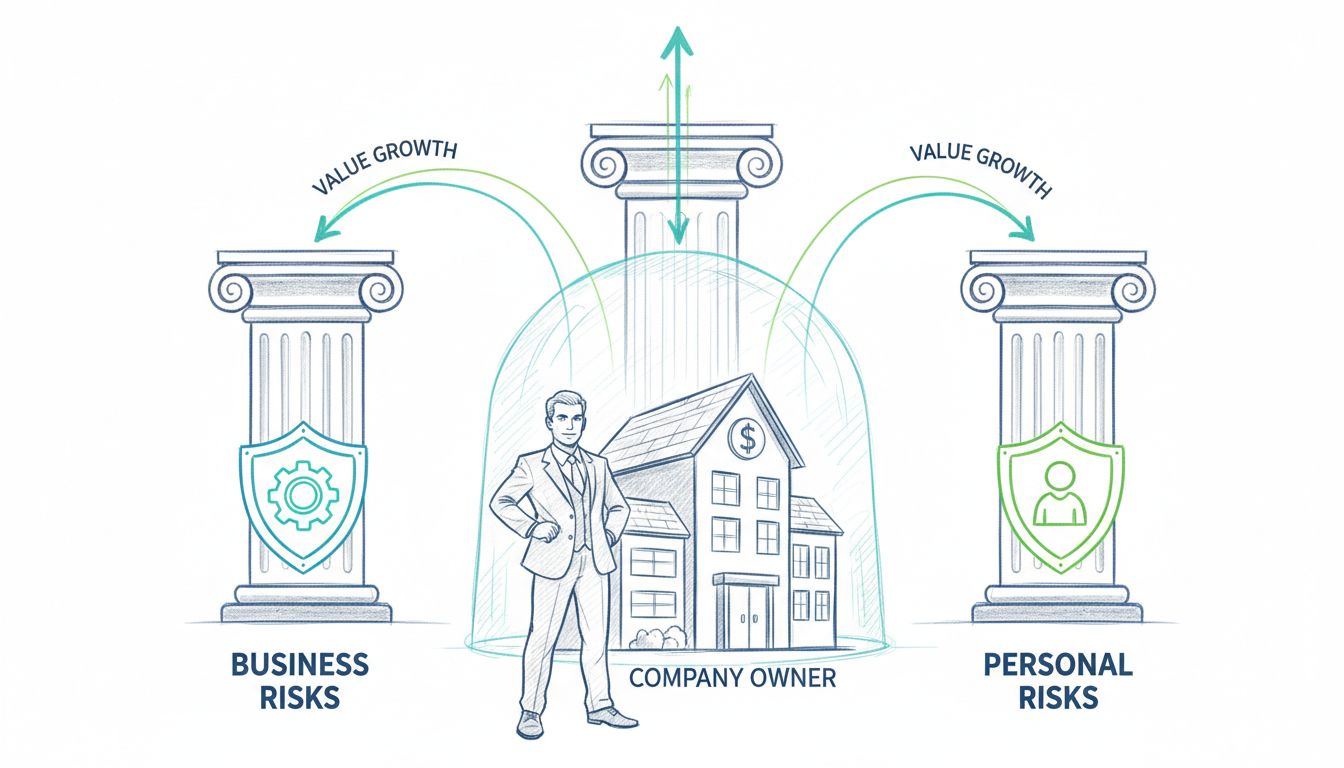
Learn why protecting your business is crucial for a successful sale. Discover risk management strategies, asset protection, and valuation enhancement techniques...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.