How to Enable 2-Step Verification in Post Affiliate Pro - Complete Setup Guide
Learn how to enable two-factor authentication (2FA) in Post Affiliate Pro merchant panel. Step-by-step guide covering TOTP authenticator apps and SMS verificati...

Learn what multi-factor authentication (MFA) is and why it’s essential for security. Discover how MFA protects against phishing, credential theft, and unauthorized access in 2025.
MFA adds an extra layer of login security by requiring users to provide additional verification, such as a code sent to their phone, making unauthorized access much harder.
Multi-factor authentication (MFA) is a security process that requires users to provide two or more forms of verification to access an account or system. This layered approach to security significantly strengthens protection against unauthorized access by creating multiple barriers that attackers must overcome. Unlike traditional single-factor authentication that relies solely on a password, MFA combines different types of verification methods to ensure that even if one credential is compromised, the account remains protected. The fundamental principle behind MFA is that it’s exponentially harder for attackers to obtain multiple authentication factors than to steal a single password through phishing or data breaches.
The importance of MFA has become increasingly critical in 2025 as cyber threats continue to evolve and become more sophisticated. According to recent security research, MFA can prevent up to 99.2% of account compromise attacks, making it one of the most effective security measures available today. Organizations across all industries are now recognizing that password-only authentication is no longer sufficient to protect sensitive data and systems. PostAffiliatePro recognizes this critical need and integrates robust MFA capabilities into its affiliate management platform to ensure that your commission data, user accounts, and affiliate networks remain secure from unauthorized access.
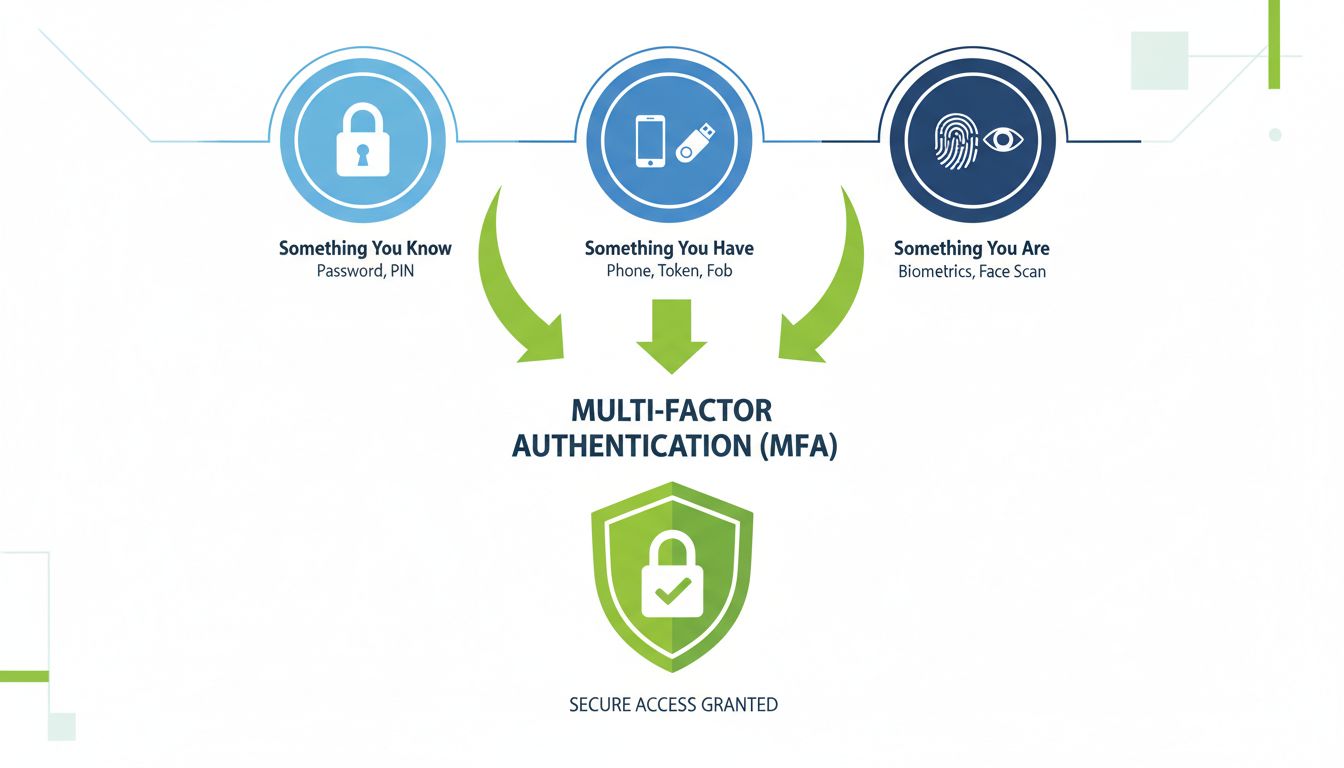
MFA relies on combining authentication factors from three distinct categories, each representing a different type of verification. This diversity ensures that compromising one factor doesn’t automatically compromise the entire authentication system. Understanding these three categories is essential for implementing effective security strategies in your organization.
Something You Know (Knowledge Factor) represents information that only the legitimate user should possess. This typically includes passwords, personal identification numbers (PINs), or answers to security questions. While knowledge factors are the most common form of authentication, they are also the most vulnerable to compromise through phishing attacks, social engineering, or data breaches. Passwords can be guessed through brute-force attacks or stolen from compromised databases. Despite these vulnerabilities, knowledge factors remain an important component of MFA because they are easy to implement and users are already familiar with them. However, they should never be used as the sole authentication method in a security-conscious organization.
Something You Have (Possession Factor) involves a physical or digital item that only the authorized user possesses. Common examples include smartphones, hardware security keys, smart cards, or security tokens. When a user attempts to log in, the system sends a verification code to their registered device, which they must then enter to complete authentication. This factor is significantly more secure than knowledge factors because it requires the attacker to physically obtain or compromise the user’s device. Possession factors are particularly effective against remote attacks because they cannot be easily replicated or stolen through digital means alone. Modern possession factors like FIDO2 security keys use cryptographic protocols that make them resistant to phishing and man-in-the-middle attacks.
Something You Are (Inherence Factor) uses biometric data unique to each individual, such as fingerprints, facial recognition, iris scans, or voice patterns. Biometric authentication is extremely difficult to forge or steal because it’s based on physical characteristics that cannot be easily changed or replicated. The inherence factor provides the highest level of security among the three categories because biometric data is unique to each person and cannot be shared or forgotten like passwords. However, biometric systems require specialized hardware and careful data protection protocols to ensure that biometric information is securely stored and processed. Organizations implementing biometric authentication must comply with privacy regulations and ensure that biometric data is encrypted and never exposed in plain text.
The cybersecurity landscape has fundamentally changed, making MFA no longer optional but absolutely essential for protecting sensitive data and systems. In 2025, organizations face unprecedented threats from sophisticated attackers who employ advanced techniques to compromise credentials and gain unauthorized access. The statistics are sobering: over 1 billion records were stolen in 2024, and credential theft remains the primary cause of data breaches across industries. Without MFA, organizations are leaving their most valuable assets vulnerable to attack.
Protection Against Credential-Based Attacks is one of the most compelling reasons to implement MFA. Cybercriminals use various techniques to obtain user credentials, including phishing emails that trick users into revealing their passwords, brute-force attacks that systematically try different password combinations, and credential stuffing attacks that use stolen credentials from one service to attempt access to other services. MFA immediately neutralizes these attacks by requiring an additional verification factor that attackers are unlikely to possess. Even if an attacker successfully steals a user’s password through phishing or a data breach, they cannot access the account without the second authentication factor. This creates a critical security boundary that stops the vast majority of credential-based attacks before they can cause damage.
Defense Against Phishing and Social Engineering is another critical benefit of MFA implementation. Phishing attacks have become increasingly sophisticated, with attackers creating convincing fake websites and emails that trick users into entering their credentials. Traditional security awareness training helps but cannot completely eliminate the risk of human error. MFA acts as a failsafe mechanism that protects accounts even when users fall victim to phishing attempts. If a user accidentally enters their credentials on a fake website, the attacker still cannot complete the login process without the second authentication factor. This significantly reduces the success rate of phishing campaigns and makes attacking individual users far less profitable for cybercriminals.
Minimization of Data Breach Impact is a crucial consideration for organizations handling sensitive information. When a data breach occurs and user credentials are exposed, MFA prevents attackers from immediately using those stolen credentials to access accounts. This containment capability limits the overall impact of a breach and provides organizations with time to detect the compromise and take remedial action. Without MFA, a single data breach can lead to widespread account takeovers and lateral movement through organizational systems. With MFA in place, even if credentials are compromised, the attacker must overcome additional security barriers to gain access.
| MFA Method | Security Level | User Convenience | Vulnerability to Phishing | Best Use Case |
|---|---|---|---|---|
| Hardware Security Keys (FIDO2) | Phishing Resistant | Moderate | Very Low | High-value accounts, admin access |
| Authenticator Apps (TOTP) | High | High | Low | General user access, remote workers |
| Push Notifications | Moderate-High | Very High | Moderate | Mobile-first organizations |
| Biometric Authentication | High | Very High | Very Low | Consumer applications, mobile devices |
| SMS One-Time Passwords | Low | High | High | Legacy systems, basic protection |
| Email One-Time Passwords | Very Low | Moderate | Very High | Not recommended for sensitive systems |
Different MFA methods offer varying levels of security and user convenience, and organizations must carefully evaluate which methods best suit their specific needs and risk profile. Hardware Security Keys like FIDO2-compliant devices represent the gold standard for MFA security because they use public-key cryptography to cryptographically bind authentication to the legitimate website. This makes them virtually immune to phishing attacks because the key will not authenticate to an incorrect domain. However, hardware keys require users to carry a physical device and may have higher implementation costs. Authenticator Apps such as Google Authenticator or Microsoft Authenticator generate time-based one-time passwords (TOTP) that are valid for only 30 seconds. These apps provide an excellent balance of security and convenience because they don’t rely on cellular networks and are resistant to SIM-swapping attacks. Push Notifications send an approval request directly to a user’s mobile device, allowing them to approve or deny access with a single tap. This method offers exceptional user convenience but can be vulnerable to MFA fatigue attacks where attackers bombard users with notifications hoping for an accidental approval.
Biometric Authentication methods including fingerprint scans, facial recognition, and voice authentication provide both high security and excellent user experience. Biometrics are difficult to forge or steal, and users find them intuitive and fast to use. However, biometric systems require specialized hardware and careful implementation to ensure that biometric data is securely stored and protected. SMS and Email-based One-Time Passwords are the most widely deployed MFA methods due to their simplicity and low implementation cost, but they are also the least secure. SMS codes can be intercepted through SIM-swapping attacks or network interception, and email-based codes are vulnerable if the user’s email account is compromised. Organizations should consider phasing out these weaker methods in favor of more secure alternatives, especially for high-value accounts and sensitive systems.
Successful MFA implementation requires careful planning, strategic rollout, and ongoing management to maximize security benefits while maintaining user adoption. Organizations should begin by conducting a comprehensive risk assessment to identify their most critical assets and determine which users and systems require MFA protection. A phased rollout approach, starting with high-risk users and sensitive systems, allows organizations to test their MFA solution, gather user feedback, and make adjustments before expanding to the entire organization. This incremental approach minimizes disruption and increases the likelihood of successful adoption.
User Training and Support are critical factors in MFA success because user resistance and confusion can undermine even the best technical implementation. Organizations should provide clear, step-by-step instructions for MFA enrollment and use, emphasizing the security benefits and addressing common concerns. Establishing robust support channels, such as a dedicated help desk or IT support team, ensures that users can quickly resolve MFA-related issues and reduces workarounds that could compromise security. Integration with Existing Systems is essential for seamless MFA deployment. Organizations should integrate MFA directly with their Identity Provider (IdP) such as Azure Active Directory, Okta, or Ping Identity to ensure consistent enforcement across all connected applications. This centralized approach simplifies user management and reduces the complexity of maintaining multiple MFA systems.
Adaptive MFA Policies represent the next evolution in authentication security, using contextual information such as user location, device type, and login history to dynamically adjust authentication requirements. Adaptive MFA can increase security for high-risk scenarios, such as login attempts from unusual locations or unknown devices, while minimizing friction for routine access from trusted devices. This intelligent approach balances security with user convenience and has been shown to significantly improve both security outcomes and user satisfaction. Organizations should also implement Conditional Access Policies that trigger additional authentication steps only when necessary, such as when accessing highly sensitive data or performing critical operations.
The field of authentication is rapidly evolving, with new technologies and approaches emerging to address the limitations of traditional MFA methods. Adaptive and AI-Enhanced Authentication uses machine learning algorithms to analyze user behavior patterns and detect anomalies that might indicate a compromise or attack. These systems can assign real-time risk scores to authentication attempts based on numerous data points, including historical login behavior, IP reputation, and known threat intelligence. Based on the risk score, the system can automatically adjust authentication requirements, deny access to high-risk attempts, or escalate alerts to security teams. This proactive approach to security significantly improves threat detection and response times.
Passwordless Authentication represents a significant shift in how organizations approach security by eliminating passwords entirely in favor of stronger authentication methods. Passwordless approaches use FIDO2 keys, biometrics, or other phishing-resistant methods as the primary authentication factor, removing the weakest link in traditional authentication chains. This approach has been shown to reduce phishing attacks by up to 99% and significantly improves user experience by eliminating the need to remember complex passwords. Continuous Authentication extends MFA beyond the initial login by continuously verifying the user’s identity throughout their session. This involves ongoing monitoring of behavioral signals, device characteristics, and contextual factors to ensure that the person using the account remains the legitimate user. If the system detects significant changes in behavior or environment, it can trigger re-authentication or restrict access to sensitive operations.
In 2025, MFA implementation is no longer a competitive advantage but a regulatory requirement for most organizations. HIPAA (Health Insurance Portability and Accountability Act) requires healthcare organizations to implement strong authentication controls to protect patient health information. PCI DSS (Payment Card Industry Data Security Standard) mandates MFA for access to payment systems and cardholder data. GDPR (General Data Protection Regulation) requires organizations to implement appropriate technical and organizational measures to protect personal data, with MFA being a key control. NIST (National Institute of Standards and Technology) guidelines recommend MFA as a fundamental security control for protecting federal information systems. Organizations that fail to implement MFA may face significant regulatory penalties, legal liability, and reputational damage.
PostAffiliatePro helps organizations meet these compliance requirements by providing enterprise-grade MFA capabilities that integrate seamlessly with existing security infrastructure. Our platform supports multiple MFA methods, adaptive authentication policies, and comprehensive audit logging to demonstrate compliance with regulatory frameworks. By implementing MFA through PostAffiliatePro, organizations can protect their affiliate networks, commission data, and user accounts while meeting the stringent security requirements of modern regulatory environments.
Multi-factor authentication has become an essential security control that organizations cannot afford to ignore in 2025. By requiring users to provide multiple forms of verification, MFA creates a layered defense that is exponentially more difficult for attackers to overcome than traditional password-only authentication. The combination of knowledge factors, possession factors, and inherence factors provides comprehensive protection against credential-based attacks, phishing, social engineering, and data breaches. Organizations that implement MFA significantly reduce their security risk, improve their compliance posture, and demonstrate a commitment to protecting sensitive data and systems.
The choice of MFA methods should be based on a careful assessment of organizational risk, user needs, and compliance requirements. While SMS-based codes provide basic protection, phishing-resistant methods like FIDO2 security keys offer superior security for high-value accounts. Adaptive MFA policies that adjust authentication requirements based on contextual factors provide an optimal balance between security and user convenience. As threats continue to evolve and regulatory requirements become more stringent, organizations that prioritize MFA implementation will be better positioned to protect their assets and maintain the trust of their customers and partners.
Protect your affiliate program with enterprise-grade security features including multi-factor authentication. PostAffiliatePro provides comprehensive security controls to safeguard your commission data and user accounts from unauthorized access.
Learn how to enable two-factor authentication (2FA) in Post Affiliate Pro merchant panel. Step-by-step guide covering TOTP authenticator apps and SMS verificati...
Learn how to enable 2-step verification (2FA) for both merchants and affiliates in Post Affiliate Pro. Secure your account with authentication apps, understand ...
Discover why multi-touch attribution is essential for modern marketing. Learn how it improves budget allocation, ROI measurement, and customer insights across y...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.