What Does a Web Host Do? Complete Guide to Web Hosting Services
Learn what web hosts do, how they work, and why they're essential for your online presence. Discover hosting types, features, and how PostAffiliatePro can help ...

Learn how firewalls serve as the first line of defense against data breaches in 2025. Discover firewall types, security mechanisms, and best practices for protecting your network infrastructure.
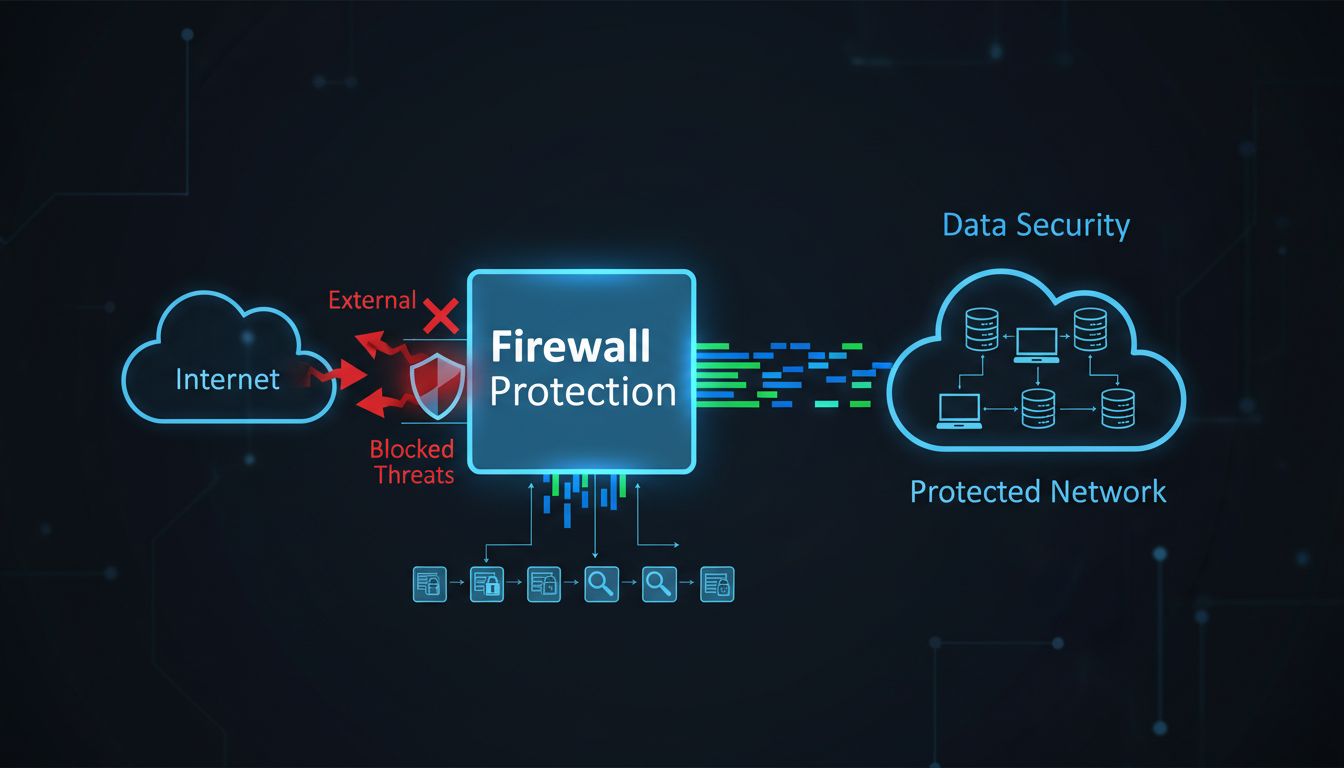
Firewalls act as the first line of defense by monitoring data flow between your network and the internet, screening out suspicious activity and blocking unauthorized access before threats can infiltrate your systems.
Firewalls represent one of the most critical components of modern cybersecurity infrastructure, serving as the essential barrier between your trusted internal network and the untrusted external internet. A firewall is fundamentally a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules and policies. By examining each data packet that attempts to cross the network boundary, firewalls make real-time decisions about whether to allow or block traffic, effectively preventing unauthorized access and malicious content from reaching your systems. This gatekeeping function has remained central to network security for over 25 years, and despite the evolution of cyber threats, firewalls continue to be indispensable in any comprehensive security strategy.
The primary mechanism through which firewalls protect against data breaches involves traffic filtering and inspection. When data attempts to enter or exit your network, the firewall examines the packet headers and content, comparing them against established security rules. These rules typically specify which IP addresses, ports, and protocols are permitted or denied. By implementing a “deny by default, allow by exception” approach, organizations can ensure that only explicitly authorized traffic passes through the firewall, dramatically reducing the attack surface available to potential threat actors. This proactive filtering capability means that many common attack vectors—including malware, unauthorized access attempts, and data exfiltration—are stopped before they can compromise your network infrastructure.
Modern firewalls employ sophisticated monitoring techniques to examine network traffic at multiple layers of the OSI model. At the most basic level, packet-filtering firewalls analyze packet headers containing source and destination IP addresses, port numbers, and protocol types. However, contemporary firewalls have evolved far beyond simple packet inspection to include stateful inspection capabilities that track the state of network connections throughout their entire lifecycle. This means firewalls can understand the context of network communications, distinguishing between legitimate traffic that is part of an established connection and suspicious traffic that attempts to initiate unauthorized connections. Stateful inspection firewalls maintain connection tables that record active sessions, allowing them to make more intelligent decisions about which packets belong to legitimate conversations and which represent potential threats.
Deep packet inspection (DPI) represents another critical advancement in firewall technology, enabling firewalls to examine not just packet headers but also the actual content or payload of data packets. This capability allows firewalls to identify and block specific types of threats that might be hidden within seemingly legitimate traffic, such as malware embedded in files, SQL injection attacks within web requests, or sensitive data attempting to leave the network. By analyzing the actual data being transmitted, firewalls can enforce more granular security policies and prevent sophisticated attacks that would bypass traditional header-based filtering. Additionally, modern firewalls can perform application-layer inspection, understanding which specific applications are generating network traffic and enforcing application-specific security policies. This means a firewall can allow web browsing traffic while blocking file-sharing applications, or permit email while restricting instant messaging, providing organizations with precise control over network usage.
The firewall landscape has evolved significantly, with different types of firewalls offering varying levels of protection and sophistication. Understanding these different firewall types helps organizations select the most appropriate solution for their specific security requirements and network architecture.
| Firewall Type | Key Characteristics | Best Use Case | Protection Level |
|---|---|---|---|
| Packet-Filtering Firewalls | Examines packet headers only; simple rule-based filtering | Small networks with basic security needs | Basic |
| Stateful Inspection Firewalls | Tracks connection states; understands context | Traditional corporate networks | Intermediate |
| Proxy Firewalls | Acts as intermediary; inspects at application layer | Organizations requiring content filtering | Intermediate |
| Next-Generation Firewalls (NGFW) | Includes IPS, URL filtering, malware prevention, application awareness | Enterprise networks with complex requirements | Advanced |
| Web Application Firewalls (WAF) | Specialized protection for web applications; defends against application-layer attacks | Organizations hosting web applications and APIs | Specialized |
| AI-Powered Firewalls | Uses machine learning to detect anomalies and novel threats | Organizations facing advanced persistent threats | Advanced |
Next-generation firewalls (NGFWs) represent the current standard for enterprise network protection, combining traditional firewall capabilities with intrusion prevention systems (IPS), URL filtering, malware defense, and application visibility and control. NGFWs can identify the specific applications generating network traffic and enforce policies based on application type rather than just port numbers, which is crucial since modern threats often use standard ports to evade detection. These firewalls integrate threat intelligence feeds that provide real-time information about emerging threats, allowing them to block known malicious IP addresses and domains automatically. Furthermore, NGFWs can perform SSL/TLS inspection, decrypting encrypted traffic to examine its contents for threats before re-encrypting it, ensuring that malicious content cannot hide within encrypted communications.
While firewalls serve as the first line of defense, security experts emphasize that firewalls alone are insufficient to protect against the full spectrum of modern cyber threats. Advanced persistent threats (APTs), insider threats, and zero-day vulnerabilities can potentially bypass or circumvent firewall protections, which is why organizations must implement defense-in-depth strategies that layer multiple security controls. When firewalls are deployed at the network perimeter, they provide visibility into all traffic entering and leaving the organization, enabling them to block the majority of external threats before they reach internal systems. However, for threats that manage to cross the network boundary, internal firewalls can segment the network into smaller zones, making it more difficult for attackers to move laterally and access sensitive data.
Network segmentation using internal firewalls creates compartmentalized security zones where different levels of trust and access controls apply. For example, a firewall might separate the general user network from the database server network, requiring explicit authorization for any communication between these zones. This approach significantly limits the damage an attacker can cause if they compromise a user workstation, as they cannot automatically access critical systems without passing through additional firewall checkpoints. Identity-based inspection capabilities in modern firewalls add another layer of sophistication by allowing access control decisions based on user identity and role rather than just network location. This means a firewall can enforce policies like “only finance department users can access the accounting database” or “only authorized administrators can access the configuration management system,” providing granular control over who can access what resources.
Effective firewall deployment requires careful planning and ongoing management to maintain security effectiveness. Organizations should begin by establishing clear security policies that define which types of traffic are permitted and which are denied, with a preference for denying all traffic by default and explicitly allowing only necessary communications. Firewall rules should be as specific as possible, avoiding overly broad rules that might inadvertently allow malicious traffic or create security gaps. For example, instead of allowing all traffic from a particular IP range, organizations should specify the exact ports and protocols required for legitimate business communications. Regular audits of firewall rules are essential, as rules often accumulate over time and outdated or redundant rules can create security vulnerabilities or degrade firewall performance.
Firewall updates and patches must be applied promptly to address newly discovered vulnerabilities in the firewall software itself. Like any software, firewalls can contain security flaws that attackers might exploit to bypass protections, making timely patching critical to maintaining security. Organizations should implement a change management process for firewall updates that balances security with operational stability, testing updates in non-production environments before deploying them to production firewalls. Continuous monitoring of firewall logs and alerts provides visibility into attempted attacks and suspicious activities, allowing security teams to identify emerging threats and adjust firewall rules accordingly. Many organizations implement Security Information and Event Management (SIEM) systems that aggregate firewall logs with other security data, enabling correlation analysis that can detect sophisticated multi-stage attacks that might not be apparent from firewall logs alone.
The threat landscape continues to evolve, with attackers developing increasingly sophisticated techniques to evade traditional firewall protections. Encrypted traffic has become ubiquitous, with the majority of internet traffic now using HTTPS or other encryption protocols, making it impossible for firewalls to inspect encrypted content without decryption capabilities. This has driven the development of firewalls with SSL/TLS inspection capabilities, though implementing such inspection requires careful consideration of privacy implications and performance impacts. Zero-day vulnerabilities—security flaws unknown to vendors and therefore unpatched—represent another challenge, as firewalls cannot block attacks exploiting vulnerabilities they have no knowledge of. To address this, modern firewalls increasingly incorporate behavioral analysis and anomaly detection capabilities that can identify suspicious activities even when the specific attack technique is unknown.
Artificial intelligence and machine learning are transforming firewall capabilities, enabling systems to learn from historical data and identify novel attack patterns that deviate from normal network behavior. AI-powered firewalls can analyze vast amounts of network traffic data to establish baselines of normal activity, then flag deviations that might indicate compromise or attack. These systems can adapt to new threats in real-time without requiring manual rule updates, providing protection against emerging threats that traditional rule-based firewalls might miss. Additionally, cloud-based and virtual firewall deployments have become increasingly important as organizations adopt hybrid and multi-cloud architectures, requiring firewalls that can protect applications and data regardless of whether they reside on-premises, in public clouds, or in private cloud environments.
Many regulatory frameworks and industry standards mandate the implementation of firewalls as a fundamental security control. Compliance requirements such as PCI DSS (Payment Card Industry Data Security Standard), HIPAA (Health Insurance Portability and Accountability Act), and GDPR (General Data Protection Regulation) all require organizations to implement firewalls as part of their security infrastructure. These regulations recognize that firewalls are essential for protecting sensitive data and preventing unauthorized access, making firewall implementation not just a security best practice but a legal requirement for many organizations. Beyond regulatory compliance, firewalls help organizations meet industry-specific security standards and frameworks such as ISO 27001, NIST Cybersecurity Framework, and CIS Controls, which all emphasize the importance of network perimeter protection.
Organizations should document their firewall configurations, rules, and security policies to demonstrate compliance with applicable regulations and standards. This documentation serves multiple purposes: it provides evidence of security controls for auditors and regulators, facilitates knowledge transfer when security personnel change, and enables consistent enforcement of security policies across the organization. Regular security assessments and penetration testing should include evaluation of firewall effectiveness, ensuring that firewalls are properly configured and functioning as intended. Third-party security assessments can provide independent verification that firewall protections meet regulatory requirements and industry best practices, identifying any gaps or misconfigurations that might leave the organization vulnerable to data breaches.
Firewalls remain the cornerstone of network security in 2025, providing essential protection against the vast majority of external threats attempting to breach organizational networks. By monitoring and filtering all traffic crossing the network boundary, firewalls prevent unauthorized access, block malware, and protect sensitive data from exfiltration. However, organizations must recognize that firewalls are one component of a comprehensive security strategy that should also include endpoint protection, intrusion detection systems, security awareness training, and incident response capabilities. The evolution of firewall technology—from simple packet filters to AI-powered systems capable of detecting novel threats—demonstrates the ongoing commitment to staying ahead of emerging cyber threats.
For organizations seeking to enhance their security posture, implementing or upgrading firewalls should be a priority, with particular attention to deploying next-generation firewalls that offer advanced threat protection capabilities. Regular maintenance, monitoring, and updates ensure that firewalls continue to provide effective protection as the threat landscape evolves. By combining robust firewall protections with other security controls and maintaining a security-conscious organizational culture, businesses can significantly reduce their risk of data breaches and protect their most valuable assets from cyber threats.
Just as firewalls protect networks from breaches, PostAffiliatePro protects your affiliate program with enterprise-grade security, fraud detection, and data protection. Secure your affiliate operations today.
Learn what web hosts do, how they work, and why they're essential for your online presence. Discover hosting types, features, and how PostAffiliatePro can help ...
Learn how to check server hits with comprehensive methods including access logs, web server analysis tools, and real-time traffic monitoring. Expert guide for a...
Learn what whitelisting means in cybersecurity, how it works, and why it's essential for affiliate marketing security. Discover whitelist vs blacklist strategie...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.